Question 21
Which of the following attack methods is to construct special SQL statements and submit sensitive information to exploit program vulnerabilities
Question 22
A Web server is deployed in an enterprise intranet to provide Web access services to Internet users, and in order to protect the access security of the server, it should be divided into the _____ area of the firewall.
Question 23
As shown in the figure, what is the range of the AH protocol authentication range in transmission mode?
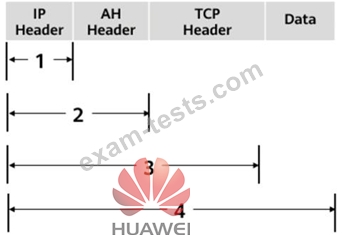

Question 24
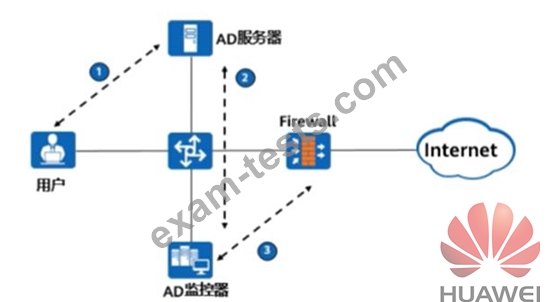
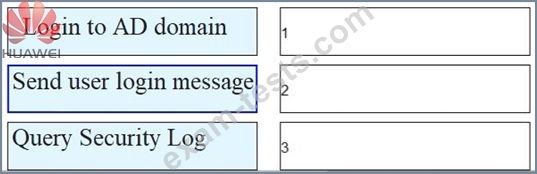
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.


Question 25
In the Linux system, which of the following is the command to query the P address information? ( )[Multiple choice]*


