Question 71
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
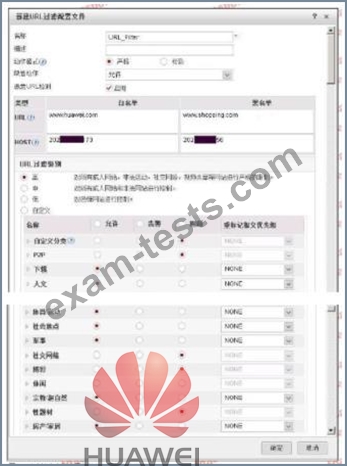

Question 72
The administrator has made the following configuration:
1. The signature set Protect_ all includes the signature ID3000, and the overall action of the signature set is to block.
2. The action of overwriting signature ID3000 is an alarm.
1. The signature set Protect_ all includes the signature ID3000, and the overall action of the signature set is to block.
2. The action of overwriting signature ID3000 is an alarm.
Question 73
Network attacks are mainly divided into two categories: single-packet attacks and streaming attacks.
Single-packet attacks include scanning and snooping attacks, malformed packet attacks, and special reports.
Wen attack.
Single-packet attacks include scanning and snooping attacks, malformed packet attacks, and special reports.
Wen attack.
Question 74
The whitelist rule of the firewall antivirus module is configured as *example*. Which of the following matches is used in this configuration?
Question 75
When using the two-way SSL function to decrypt HTTPS packets, the value of the reverse proxy level represents the number of times the packet can be decrypted.

