Question 106
Malicious code usually uses RootKit technology to hide itself. RootKit modifies the kernel of the system by loading special drivers to hide itself and specific files.
Question 107
Huawei NIP6000 products provide carrier-class high-reliability mechanisms from multiple levels to ensure the stable operation of equipment.
Which of the following options belong to the network reliability? (multiple choice)
Which of the following options belong to the network reliability? (multiple choice)
Question 108
Which of the following protocols can be used to construct attack messages for special control message attacks? (multiple choice)
Question 109
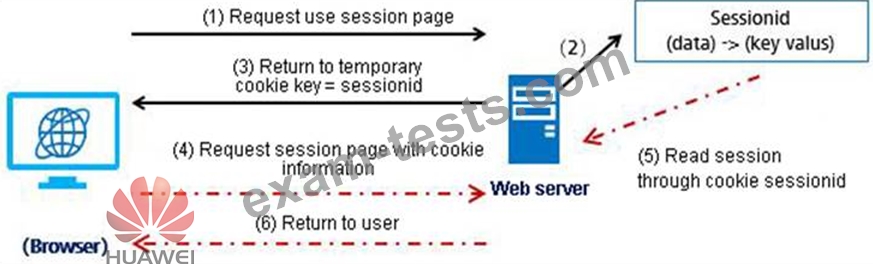
The process of a browser carrying a cookie to request a resource from a server is as shown in the following figure. Which of the following steps have the session ID information in the message?

Question 110
Because the sandbox can provide virtual execution environment to detect files on the network, the sandbox can replace devices such as Anti-Virus, IPS and spam detection when deploying security devices.

