Question 41
Cloud sandbox refers to deploying the sandbox in the cloud and providing remote detection services for tenants. The process includes:
1. Report suspicious files
2. Retrospective attack
3. Firewall linkage defense
4. Prosecution in the cloud sandbox
For the ordering of the process, which of the following options is correct?
1. Report suspicious files
2. Retrospective attack
3. Firewall linkage defense
4. Prosecution in the cloud sandbox
For the ordering of the process, which of the following options is correct?
Question 42
Which of the following options is not a cyber security threat caused by weak personal security awareness?
Question 43
In the following options, which of the two attacks use similar attack methods, they will generate a large number of useless response packets, occupying network bandwidth, Consume equipment resources?
Question 44
An enterprise administrator configures the Web reputation system as shown in the figure. Regarding the configuration, which of the following statements is correct?
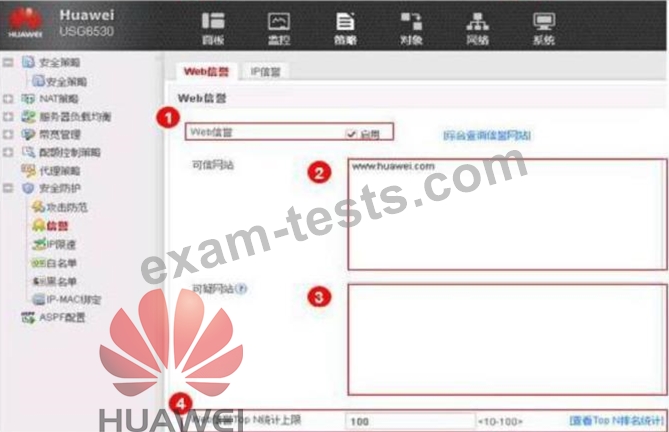

Question 45
When a data file hits the whitelist of the firewall's anti-virus module, the firewall will no longer perform virus detection on the file.

