Question 26
Part of the reason why the APT attack becomes difficult to defend is that it uses the vulnerabilities to attack.
This kind of zero-day hole usually requires flowers
A lot of time to research and analyze and produce corresponding defense methods.
This kind of zero-day hole usually requires flowers
A lot of time to research and analyze and produce corresponding defense methods.
Question 27
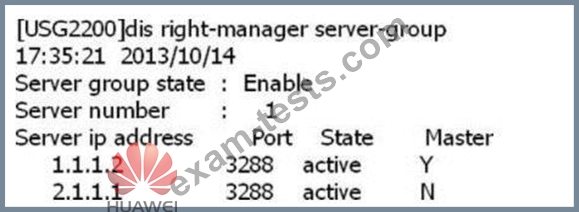
SACG query right-manager information as follows, which options are correct? (Select 2 answers)

Question 28
Which of the following behaviors is a false positive of the intrusion detection system?
Question 29
Which of the following statements about IPS is wrong?
Question 30
Regarding intrusion prevention, which of the following option descriptions is wrong

