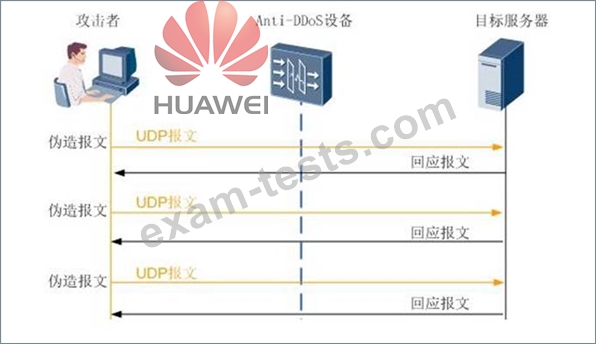
Question 31
As shown in the figure, the corresponding defense methods are:

Question 32
An FTP server ( DMZ ) on the existing network of the enterprise provides FTP services to the outside ( Untrust ), and a USG firewall is deployed on the external network port.
The following information is obtained by capturing packets on the FTP server:
Sequence Number Source Address Destination Address Protocol Packet Summary
1 1.1.1.1 192.168.1.2 TCP 3318>21 [SYN] Seq=0 Len=0 MSS=1460
2 192.168.1.2 1.1.1.1 TCP 21>3318 [SYN, ACK] Seq=0 Ack=1 Win=65535 Len=0 MSS=1460
3 1.1.1.1 192.168.1.2 TCP 3318>21[SYN] Seq=1 Ack=1 Win=65535 Len=0
......
13 1.1.1.1 192.168.1.2 FTP Request: PASV
14 192.168.1.2 1.1.1.1 FTP Response: 227 Entering Passive Mode (192, 168, 1, 2, 4, 162)
15 1.1.1.1 192.168.1.2 TCP 3319>1186 [SYN] Seq=0 Len=0 MSS=1460
16 192.168.1.2 1.1.1.1 TCP 1186>3319 [SYN, ACK] Seq=0 Ack=1 Win=65535 Len=0 MSS=1460
17 1.1.1.1 192.168.1.2 TCP 3319>1186 [SYN] Seq=1 Ack=1 Win=65535 Len=0
.....
The following descriptions are correct:
The following information is obtained by capturing packets on the FTP server:
Sequence Number Source Address Destination Address Protocol Packet Summary
1 1.1.1.1 192.168.1.2 TCP 3318>21 [SYN] Seq=0 Len=0 MSS=1460
2 192.168.1.2 1.1.1.1 TCP 21>3318 [SYN, ACK] Seq=0 Ack=1 Win=65535 Len=0 MSS=1460
3 1.1.1.1 192.168.1.2 TCP 3318>21[SYN] Seq=1 Ack=1 Win=65535 Len=0
......
13 1.1.1.1 192.168.1.2 FTP Request: PASV
14 192.168.1.2 1.1.1.1 FTP Response: 227 Entering Passive Mode (192, 168, 1, 2, 4, 162)
15 1.1.1.1 192.168.1.2 TCP 3319>1186 [SYN] Seq=0 Len=0 MSS=1460
16 192.168.1.2 1.1.1.1 TCP 1186>3319 [SYN, ACK] Seq=0 Ack=1 Win=65535 Len=0 MSS=1460
17 1.1.1.1 192.168.1.2 TCP 3319>1186 [SYN] Seq=1 Ack=1 Win=65535 Len=0
.....
The following descriptions are correct:
Question 33
Which of the following descriptions are correct about the way SAC devices are connected to the network?
Question 34
The USG serves as the gateway of the headquarters. Users on business trips need to use the Internet to establish a VPN tunnel to access the resources of the headquarters, and users on business trips do not need to install any dial-up software. Which of the following VPN technologies is most suitable:
Question 35
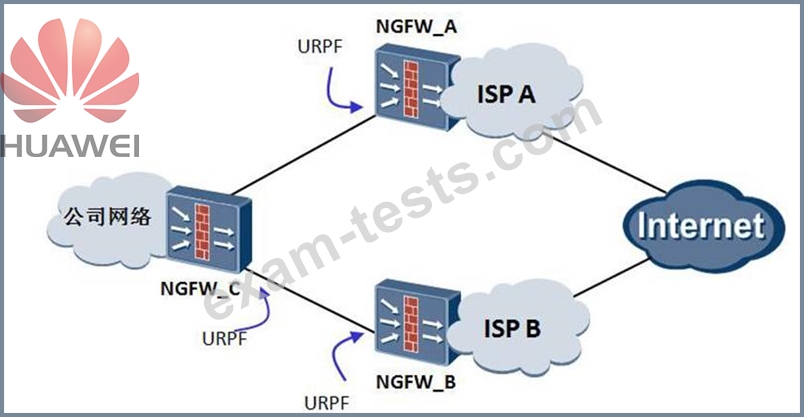
A network expects to use URPF technology to improve network security. Which mode of URPF is used in the following networking scenarios: