Question 21
Regarding the relationship between 802.1X and RADIUS, which of the following descriptions is correct?
Question 22
Which of the following tasks need to be completed before configuring an IPsec security policy?
Question 23
The anti-spam function of Huawei firewall uses the RBL method. What are the requirements for the DNS server?
Question 24
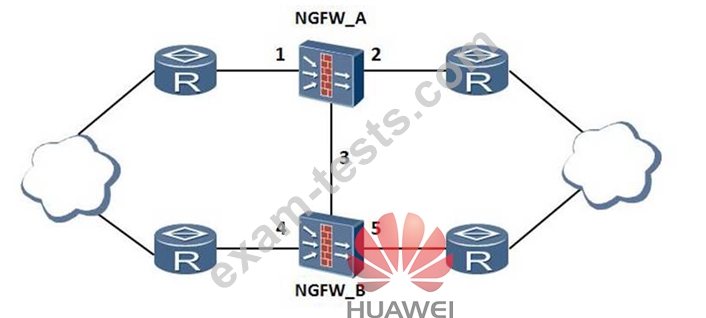
A network needs to replace the dual-system hot-standby USG_A and USG_B due to the network upgrade of the new hardware USG. Without affecting the business, how to upgrade:
USG_A is the Active device, and USG_B is the Standby device.
Which of the following are the correct cutover steps?
① Connect the 5th line to the new USG_B in turn.
② Connect lines 1 , 2 , and 3 from the old USG_A to the new USG A in turn,
③ Power on the new USG_B and the new USG_A, and import the configuration.
④ Input undo hrp enable in USG_B, and cut off lines 4, 5, and 3 in turn.
⑤ Adjust the routing cost so that all traffic passes through USB_B.
⑥ Enter hrp enable for new USG_A and new USG_B to adjust routing cost to meet expectations.
USG_A is the Active device, and USG_B is the Standby device.
Which of the following are the correct cutover steps?
① Connect the 5th line to the new USG_B in turn.
② Connect lines 1 , 2 , and 3 from the old USG_A to the new USG A in turn,
③ Power on the new USG_B and the new USG_A, and import the configuration.
④ Input undo hrp enable in USG_B, and cut off lines 4, 5, and 3 in turn.
⑤ Adjust the routing cost so that all traffic passes through USB_B.
⑥ Enter hrp enable for new USG_A and new USG_B to adjust routing cost to meet expectations.

Question 25
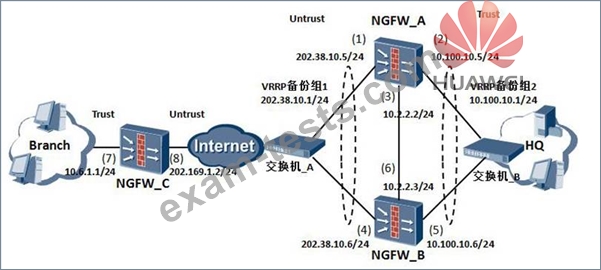
IPsec tunnel communication is used between the headquarters and branch offices, in order to ensure the security of data transmission on the Internet. The administrator uses the dual-system hot backup function to improve the reliability of the communication between the headquarters and the branch offices, so as to avoid the failure of one USG in the headquarters and the failure of the branch offices to access the headquarters.
According to the following network diagram, which of the following statements is correct?
According to the following network diagram, which of the following statements is correct?


