Question 11
Refer to the exhibits.
Exhibit 1
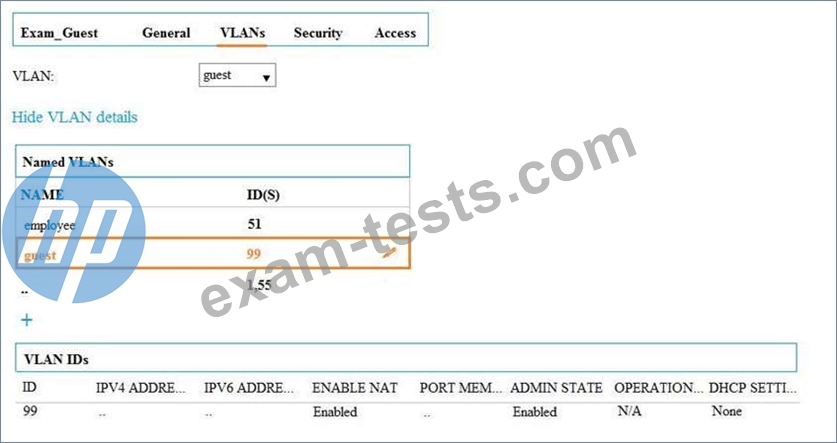
Exhibit 2

A network administrator configures a guest WLAN on an Aruba Mobility Master (MM)-based solution. The exhibits show some of the settings for this WLAN.
Which settings must the administrator configure on each Mobility Controller (MC) at the device level for this configuration to function properly?
Exhibit 1

Exhibit 2

A network administrator configures a guest WLAN on an Aruba Mobility Master (MM)-based solution. The exhibits show some of the settings for this WLAN.
Which settings must the administrator configure on each Mobility Controller (MC) at the device level for this configuration to function properly?
Question 12
A WLAN in an Aruba Mobility Master (MM)-based solution uses WPA2-Enterprise security. This WLAN currently authenticates users to Active Directory (AD), and users log in with their Windows domain credentials. Network administrators now want to authenticate the Windows clients as well, based on the client Computer Names.
What should the administrators do on MM to achieve this goal?
What should the administrators do on MM to achieve this goal?
Question 13
Refer to the exhibits.
Exhibit 1
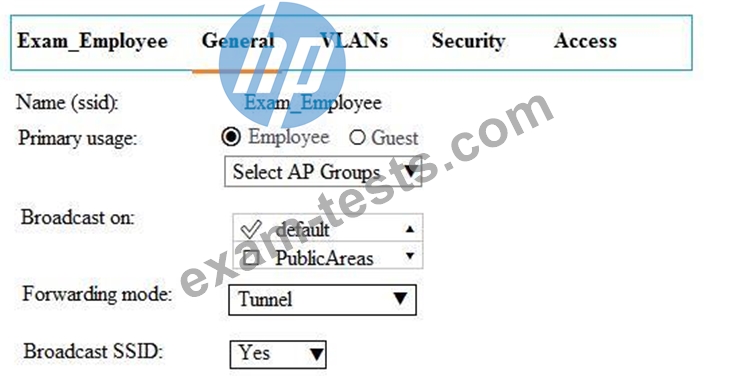
Exhibit 2
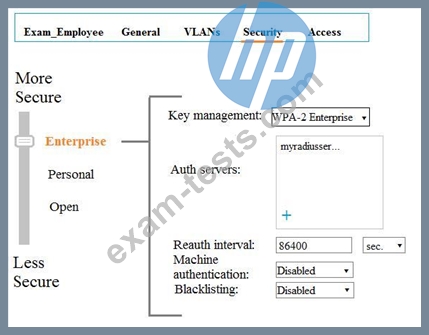
Network administrators use the Aruba Mobility Master (MM) wizard to create a WLAN and do not manually alter any of the profiles for that WLAN. The exhibits show some of the settings for the WLAN. Some wireless users cannot successfully connect to the WLAN. Network administrators attempt to connect on their own machines with a test account, and the connection is successful. They attempt to connect with the same account on user clients, and the connection fails.
Which issue could prevent authentication from completing correctly?
Exhibit 1

Exhibit 2

Network administrators use the Aruba Mobility Master (MM) wizard to create a WLAN and do not manually alter any of the profiles for that WLAN. The exhibits show some of the settings for the WLAN. Some wireless users cannot successfully connect to the WLAN. Network administrators attempt to connect on their own machines with a test account, and the connection is successful. They attempt to connect with the same account on user clients, and the connection fails.
Which issue could prevent authentication from completing correctly?
Question 14
A WLAN in an Aruba Mobility Master (MM)-based solution uses WPA2-Enterprise security. This WLAN currently authenticates users to Active Directory (AD), and users log in with their Windows domain credentials.
Network administrators now want to authenticate the Windows clients as well, based on the client Computer Names.
What should the administrator do on MM to achieve this goal?
Network administrators now want to authenticate the Windows clients as well, based on the client Computer Names.
What should the administrator do on MM to achieve this goal?
Question 15
A company has an Aruba solution with a guest WLAN named exam_guest. A network administrator creates the guest WLAN with the wizard and does not change any of the default roles. The authentication server does not send particular role assignments for authorized users. The company wants to deny guest access to specific IP rnages after the guests authenticate.
For which role should the administrator create the rule to deny this traffic?
For which role should the administrator create the rule to deny this traffic?

