Question 21
What is an example of a Layer2 wireless threat that a wireless intrusion detection system (WIDS) should detect?
Question 22
A company plans to deploy a Mobility Master (MM) solution with two MM nodes. The MM solution will manage 10 Mobility Controller (MC) appliances that will control a total of 400 APs.
How should the network administrator install the AP licenses?
How should the network administrator install the AP licenses?
Question 23
A company has a Mobility Master (MM)-based solution. How does a Mobility Controller (MC) behave if it loses contact with all MM nodes?
Question 24
What is one difference between captive portal authentication and 802.1X authentication?
Question 25
Refer to the exhibit.
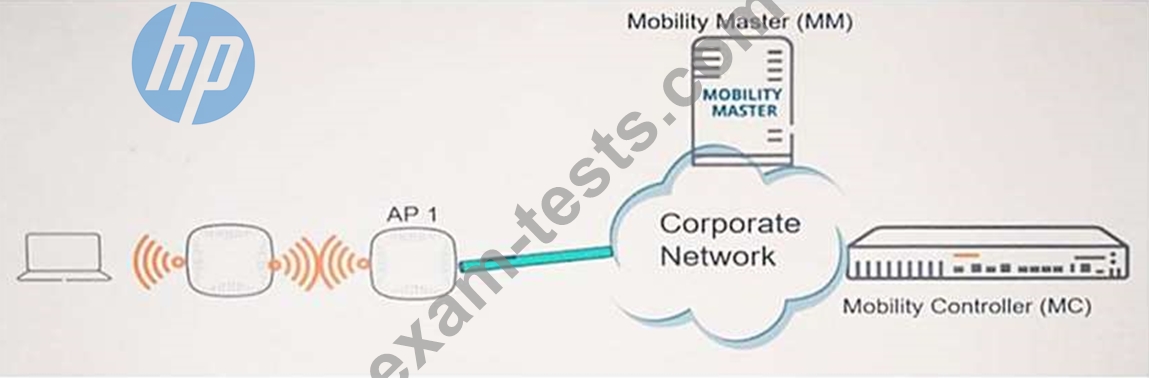
Which role must AP 1 play?

Which role must AP 1 play?

