- Home
- PECB Certification
- ISO-IEC-27001-Lead-Auditor-CN Exam
- PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166 Practice Test
Question 36
哪一項不是 HR 在招募前的要求?
Correct Answer: C
According to ISO/IEC 27001:2022, clause 7.2.2, the organization shall ensure that all persons who have access to information are aware of the information security policy and their contribution to the effectiveness of the ISMS, including the benefits of improved information security performance2. Therefore, awareness training on information security is a requirement for all persons, not just new hires. Reference: ISO/IEC 27001:2022 Lead Auditor (Information Security Management Systems) | CQI | IRCA
Question 37
您正在對位於歐洲的住宅進行 ISMS 審核
名為 ABC 的療養院提供醫療保健服務。您會發現所有療養院居民都戴著電子腕帶,用於監控他們的位置、心跳和血壓。您了解到,電子腕帶會自動將所有資料上傳到人工智慧(AI)雲端伺服器,供醫護人員進行健康監測和分析。
審核計畫的下一步是驗證高階管理人員是否已製定資訊安全策略和目標。
在審計過程中,你們發現以下審計證據。
將審核證據與 ISO/IEC 27001:2022 中的相應要求進行配對。
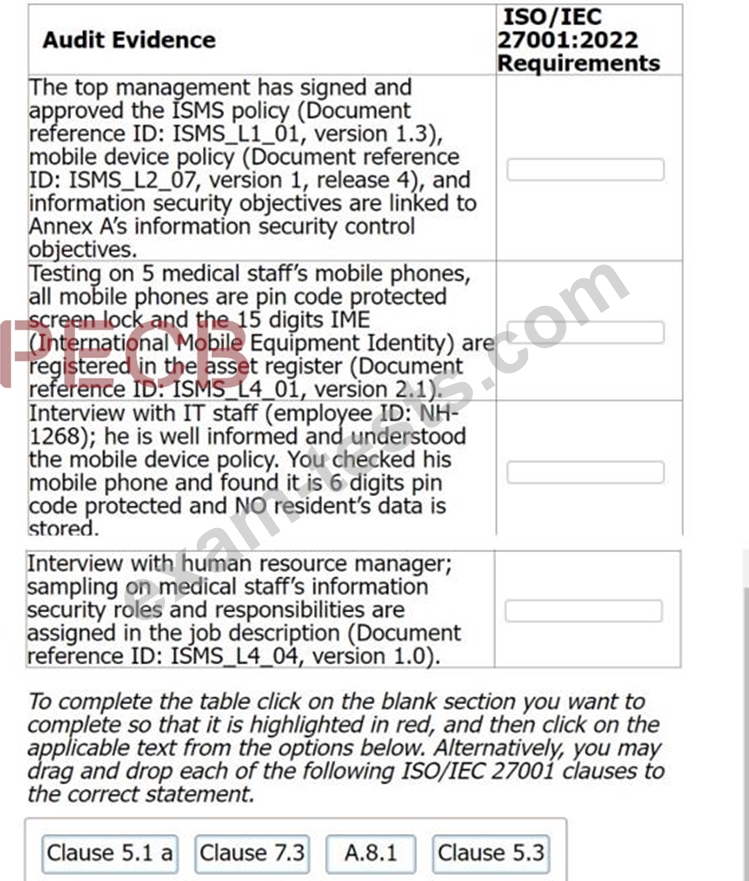
名為 ABC 的療養院提供醫療保健服務。您會發現所有療養院居民都戴著電子腕帶,用於監控他們的位置、心跳和血壓。您了解到,電子腕帶會自動將所有資料上傳到人工智慧(AI)雲端伺服器,供醫護人員進行健康監測和分析。
審核計畫的下一步是驗證高階管理人員是否已製定資訊安全策略和目標。
在審計過程中,你們發現以下審計證據。
將審核證據與 ISO/IEC 27001:2022 中的相應要求進行配對。

Correct Answer:

Question 38
您必須進行第三方虛擬審核。在開始進行審核之前,您需要告知受審核方以下哪兩個問題?
Correct Answer: C,D
A third-party virtual audit is an external audit conducted by an independent certification body using remote technology such as video conferencing, screen sharing, and electronic document exchange. The purpose of a third-party virtual audit is to verify the conformity and effectiveness of the information security management system (ISMS) and to issue a certificate of compliance12 Before you start conducting the audit, you would need to inform the auditee about the following issues: 12 You will ask those being interviewed to state their name and position beforehand, i.e., to confirm their identity and role in the ISMS. This is to ensure that you are interviewing the relevant personnel and that they are authorized to provide information and evidence for the audit.
You will ask for a 360-degree view of the room where the audit is being carried out, i.e., to verify the physical and environmental security of the audit location. This is to ensure that there are no unauthorized persons or devices in the vicinity that could compromise the confidentiality, integrity, or availability of the information being audited.
The other issues are not relevant or appropriate for a third-party virtual audit, because:
You will ask to see the ID card of the person that is on the screen, i.e., to verify their identity. This is not necessary if you have already asked them to state their name and position beforehand, and if you have access to the auditee's organizational chart or staff directory. Asking to see the ID card could also be seen as intrusive or disrespectful by the auditee.
You will take photos of every person you interview, i.e., to document the audit process. This is not advisable as it could violate the privacy or consent of the auditee and the interviewees. Taking photos could also be seen as unprofessional or suspicious by the auditee. You should rely on the audit records and evidence provided by the auditee and the audit tool instead.
You will not record any part of the audit, unless permitted, i.e., to respect the auditee's preferences and rights. This is not a valid issue to inform the auditee about, as you should always record the audit for quality assurance and verification purposes. Recording the audit is also a requirement of the ISO/IEC 27001 standard and the certification body. You should inform the auditee that you will record the audit and obtain their consent before the audit begins.
You expect the auditee to have assessed all risks associated with online activities, i.e., to ensure the security of the audit process. This is not an issue to inform the auditee about, as it is part of the auditee's responsibility and obligation to have a risk assessment and treatment process for their ISMS. You should assess the auditee's risk management practices and controls during the audit, not before it.
Reference:
1: ISO/IEC 27001:2022 Lead Auditor (Information Security Management Systems) Course by CQI and IRCA Certified Training 1 2: ISO/IEC 27001 Lead Auditor Training Course by PECB 2
You will ask for a 360-degree view of the room where the audit is being carried out, i.e., to verify the physical and environmental security of the audit location. This is to ensure that there are no unauthorized persons or devices in the vicinity that could compromise the confidentiality, integrity, or availability of the information being audited.
The other issues are not relevant or appropriate for a third-party virtual audit, because:
You will ask to see the ID card of the person that is on the screen, i.e., to verify their identity. This is not necessary if you have already asked them to state their name and position beforehand, and if you have access to the auditee's organizational chart or staff directory. Asking to see the ID card could also be seen as intrusive or disrespectful by the auditee.
You will take photos of every person you interview, i.e., to document the audit process. This is not advisable as it could violate the privacy or consent of the auditee and the interviewees. Taking photos could also be seen as unprofessional or suspicious by the auditee. You should rely on the audit records and evidence provided by the auditee and the audit tool instead.
You will not record any part of the audit, unless permitted, i.e., to respect the auditee's preferences and rights. This is not a valid issue to inform the auditee about, as you should always record the audit for quality assurance and verification purposes. Recording the audit is also a requirement of the ISO/IEC 27001 standard and the certification body. You should inform the auditee that you will record the audit and obtain their consent before the audit begins.
You expect the auditee to have assessed all risks associated with online activities, i.e., to ensure the security of the audit process. This is not an issue to inform the auditee about, as it is part of the auditee's responsibility and obligation to have a risk assessment and treatment process for their ISMS. You should assess the auditee's risk management practices and controls during the audit, not before it.
Reference:
1: ISO/IEC 27001:2022 Lead Auditor (Information Security Management Systems) Course by CQI and IRCA Certified Training 1 2: ISO/IEC 27001 Lead Auditor Training Course by PECB 2
Question 39
一個體面的訪客在沒有訪客 ID 的情況下四處閒逛。作為員工,您應該執行以下操作,但以下情況除外:
Correct Answer: A
As an employee, you should do the following when you see a visitor roaming around without visitor's ID, except saying "hi" and offering coffee. Saying "hi" and offering coffee is not an appropriate action, as it may imply that you are welcoming or endorsing the visitor without verifying their identity or purpose. This may also give the visitor an opportunity to gain your trust or exploit your kindness. Calling the receptionist and informing about the visitor is an appropriate action, as it alerts the responsible staff to handle the situation and ensure that the visitor is authorized and registered. Greeting and asking him what is his business is an appropriate action, as it shows your concern and curiosity about the visitor's presence and intention. Escorting him to his destination is an appropriate action, as it prevents the visitor from wandering around unattended and accessing unauthorized areas or information. References: : CQI & IRCA ISO 27001:2022 Lead Auditor Course Handbook, page 42. : [ISO/IEC 27001 LEAD AUDITOR - PECB], page 15.
Question 40
您是一位經驗豐富的審核團隊領導,指導審核員進行培訓。接受培訓的審核員的任務是審查適用性聲明 (SoA) 中列出的並在現場實施的技術控制措施。
從以下內容中選擇您希望接受培訓的審核員審查的四項控制措施。
從以下內容中選擇您希望接受培訓的審核員審查的四項控制措施。
Correct Answer: D,I,M,N
According to ISO/IEC 27001:2022, which specifies the requirements for establishing, implementing, maintaining and continually improving an information security management system (ISMS), an organization should select and implement appropriate controls to achieve its information security objectives1. The controls should be derived from the results of risk assessment and risk treatment, and should be consistent with the Statement of Applicability (SoA), which is a document that identifies the controls that are applicable and necessary for the ISMS1. The controls can be selected from various sources, such as ISO/IEC 27002:2013, which provides a code of practice for information security controls2. Therefore, if an auditor in training has been tasked with reviewing the technological controls listed in the SoA and implemented at the site of an organization that stores data on behalf of external clients, four controls that would be expected to review are:
How protection against malware is implemented: This is a technological control that aims to prevent, detect and remove malicious software (such as viruses, worms, ransomware, etc.) that could compromise the confidentiality, integrity or availability of information or information systems2. This control is related to control A.12.2.1 of ISO/IEC 27002:20132.
How the organisation evaluates its exposure to technical vulnerabilities: This is a technological control that aims to identify and assess the potential weaknesses or flaws in information systems or networks that could be exploited by malicious actors or cause accidental failures2. This control is related to control A.12.6.1 of ISO/IEC 27002:20132.
How access to source code and development tools are managed: This is a technological control that aims to protect the intellectual property rights and integrity of software applications or systems that are developed or maintained by the organization or its external providers2. This control is related to control A.14.2.5 of ISO/IEC 27002:20132.
The operation of the site CCTV and door control systems: This is a technological control that aims to monitor and restrict physical access to the premises or facilities where information or information systems are stored or processed2. This control is related to control A.11.1.4 of ISO/IEC 27002:20132.
The other options are not examples of technological controls, but rather organizational, legal or procedural controls that may also be relevant for an ISMS audit, but are not within the scope of the auditor in training's task. For example, the development and maintenance of an information asset inventory (related to control A.8.1.1), rules for transferring information within the organization and to other organizations (related to control A.13.2.1), confidentiality and nondisclosure agreements (related to control A.13.2.4), verification checks on personnel (related to control A.7.1.2), remote working arrangements (related to control A.6.2.1), information security within supplier agreements (related to control A.15.1.1), business continuity arrangements (related to control A.17), information deletion (related to control A.8.3), information security awareness, education and training (related to control A.7.2), equipment maintenance (related to control A.11.2), and how power and data cables enter the building (related to control A.11) are not technological controls, but rather organizational, legal or procedural controls that may also be relevant for an ISMS audit, but are not within the scope of the auditor in training's task. Reference: ISO/IEC 27001:2022 - Information technology - Security techniques - Information security management systems - Requirements, ISO/IEC 27002:2013 - Information technology - Security techniques - Code of practice for information security controls
How protection against malware is implemented: This is a technological control that aims to prevent, detect and remove malicious software (such as viruses, worms, ransomware, etc.) that could compromise the confidentiality, integrity or availability of information or information systems2. This control is related to control A.12.2.1 of ISO/IEC 27002:20132.
How the organisation evaluates its exposure to technical vulnerabilities: This is a technological control that aims to identify and assess the potential weaknesses or flaws in information systems or networks that could be exploited by malicious actors or cause accidental failures2. This control is related to control A.12.6.1 of ISO/IEC 27002:20132.
How access to source code and development tools are managed: This is a technological control that aims to protect the intellectual property rights and integrity of software applications or systems that are developed or maintained by the organization or its external providers2. This control is related to control A.14.2.5 of ISO/IEC 27002:20132.
The operation of the site CCTV and door control systems: This is a technological control that aims to monitor and restrict physical access to the premises or facilities where information or information systems are stored or processed2. This control is related to control A.11.1.4 of ISO/IEC 27002:20132.
The other options are not examples of technological controls, but rather organizational, legal or procedural controls that may also be relevant for an ISMS audit, but are not within the scope of the auditor in training's task. For example, the development and maintenance of an information asset inventory (related to control A.8.1.1), rules for transferring information within the organization and to other organizations (related to control A.13.2.1), confidentiality and nondisclosure agreements (related to control A.13.2.4), verification checks on personnel (related to control A.7.1.2), remote working arrangements (related to control A.6.2.1), information security within supplier agreements (related to control A.15.1.1), business continuity arrangements (related to control A.17), information deletion (related to control A.8.3), information security awareness, education and training (related to control A.7.2), equipment maintenance (related to control A.11.2), and how power and data cables enter the building (related to control A.11) are not technological controls, but rather organizational, legal or procedural controls that may also be relevant for an ISMS audit, but are not within the scope of the auditor in training's task. Reference: ISO/IEC 27001:2022 - Information technology - Security techniques - Information security management systems - Requirements, ISO/IEC 27002:2013 - Information technology - Security techniques - Code of practice for information security controls
- Latest Upload
- 138Fortinet.FCP_FAZ_AD-7.4.v2026-01-16.q115
- 122PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166
- 126Talend.Talend-Core-Developer.v2026-01-15.q20
- 170Salesforce.Marketing-Cloud-Administrator.v2026-01-15.q146
- 244Salesforce.ADX-211.v2026-01-14.q223
- 136Salesforce.B2B-Solution-Architect.v2026-01-14.q111
- 143BICSI.RCDD.v2026-01-14.q121
- 123NBMTM.BCMTMS.v2026-01-14.q33
- 127Microsoft.GH-200.v2026-01-13.q64
- 147SAP.C_C4HCX_2405.v2026-01-13.q80
[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor-CN.v2026-01-16.q166 Practice Test

