Question 11
Click the Exhibit button.
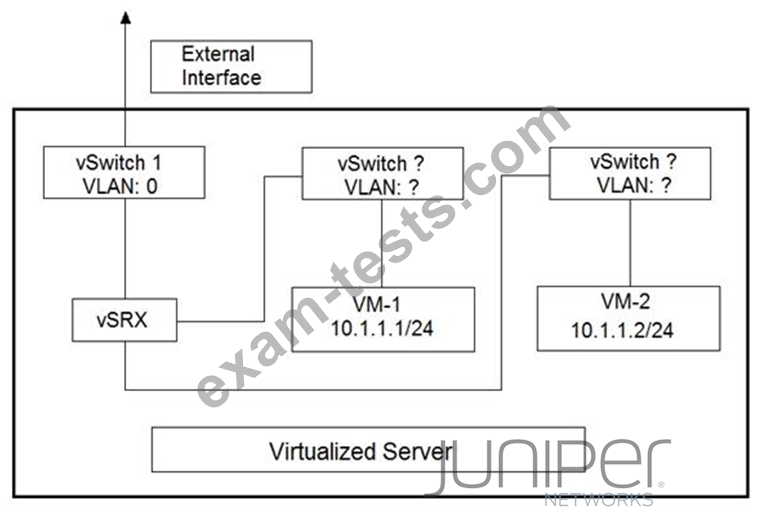
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)

You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)
Question 12
You are designing an SDSN security solution for a new campus network. The network will consist of Juniper Networks Policy Enforcer, Juniper Networks switches, third-party switches, and SRX Series devices. The switches and the SRX Series devices will be used as security enforcement points.
Which component supports the SRX Series devices in this scenario?
Which component supports the SRX Series devices in this scenario?
Question 13
You are asked to design a secure enterprise WAN where all payload data is encrypted and branch sites communicate directly without routing all traffic through a central hub.
Which two technologies would accomplish this task? (Choose two.)
Which two technologies would accomplish this task? (Choose two.)
Question 14
You are concerned about malicious attachments being transferred to your e-mail server at work through encrypted channels. You want to block these malicious files using your SRX Series device.
Which two features should you use in this scenario? (Choose two.)
Which two features should you use in this scenario? (Choose two.)
Question 15
A hosting company is migrating to cloud-based solutions. Their customers share a physical firewall cluster, subdivided into individual logical firewalls for each customer. Projection data shows that the cloud service will soon deplete all the resources within the physical firewall. As a consultant, you must propose a scalable solution that continues to protect all the cloud customers while still securing the existing physical network.
In this scenario, which solution would you propose?
In this scenario, which solution would you propose?

