Question 16
You are designing a data center security solution for a customer. The customer asks that you provide a DDoS solution. Several IPsec tunnels will be terminated at the data center gateway.
Which type of security is your customer asking you to implement?
Which type of security is your customer asking you to implement?
Question 17
You are required to design a university network to meet the conditions shown below.
Users connected to the university network should be able to access the Internet and the research department lab network.
The research department lab network should not be able to reach the Internet.
Which three actions satisfy the design requirements? (Choose three.)
Users connected to the university network should be able to access the Internet and the research department lab network.
The research department lab network should not be able to reach the Internet.
Which three actions satisfy the design requirements? (Choose three.)
Question 18
You have a site that has two Internet connections but no switch on the outside of the firewall. You want to use ISP-A over ISP-B during normal operations.
Which type of chassis cluster design would you propose to satisfy this requirement?
Which type of chassis cluster design would you propose to satisfy this requirement?
Question 19
You are working with a customer to create a design proposal using SRX Series devices. As part of the design, you must consider the requirements shown below:
* You must ensure that every packet entering your device is independently inspected against a set of rules.
* You must provide a way to protect the device from undesired access attempts.
* You must ensure that you can apply a different set of rules for traffic leaving the device than are in use for traffic entering the device.
In this scenario, what do you recommend using to accomplish these requirements?
* You must ensure that every packet entering your device is independently inspected against a set of rules.
* You must provide a way to protect the device from undesired access attempts.
* You must ensure that you can apply a different set of rules for traffic leaving the device than are in use for traffic entering the device.
In this scenario, what do you recommend using to accomplish these requirements?
Question 20
Click the Exhibit button.
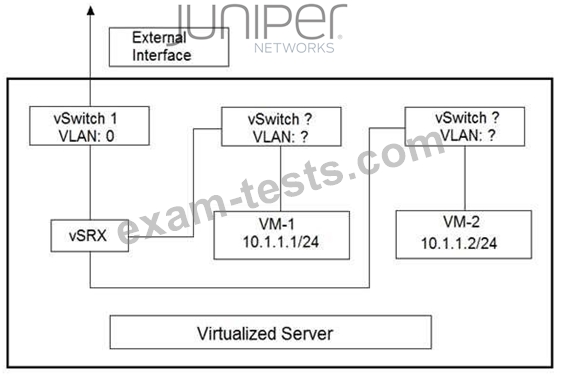
You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)

You are designing the virtualized server deployment shown in the exhibit in your data center. The vSRX device is acting as a Layer 2 firewall and the two VMs must communicate through the vSRX device.
Which two actions must you perform to accomplish this task? (Choose two.)

