Question 1
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
In this scenario, which two application security features should be used? (Choose two.)
Question 2
After performing a software upgrade on an SRX5800 chassis cluster, you notice that node1 is in the primary state and node0 is in the backup state. Your network standards dictate that node0 should be in the primary state.
In this scenario, which command should be used to comply with the network standards?
In this scenario, which command should be used to comply with the network standards?
Question 3
You want to set up JSA to collect network traffic flows from network devices on your network.
Which two statements are correct when performing this task? (Choose two.)
Which two statements are correct when performing this task? (Choose two.)
Question 4
What are two valid JIMS event log sources? (Choose two.)
Question 5
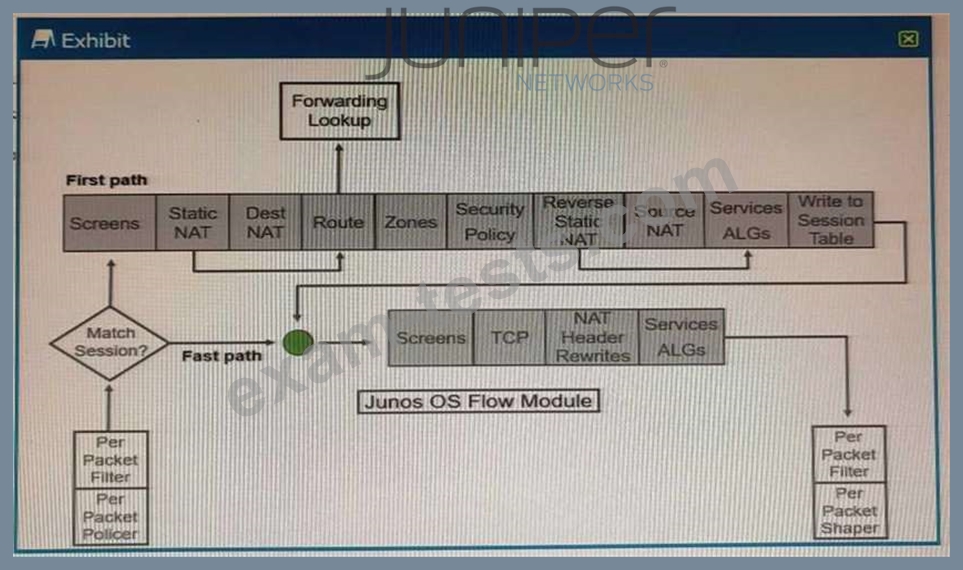
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?