Question 6
What are two types of system logs that Junos generates? (Choose two.)
Question 7
Click the Exhibit button.
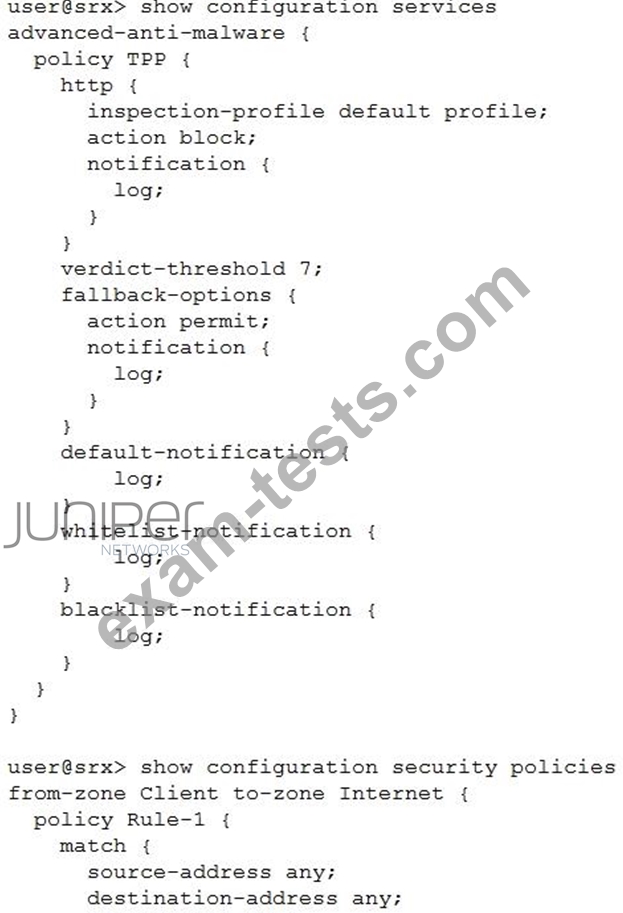
You have deployed Sky ATP to protect your network from attacks so that users are unable to download malicious files. However, after a user attempts to download a malicious file, they are still able to communicate through the SRX Series device.
Referring to the exhibit, which statement is correct?

You have deployed Sky ATP to protect your network from attacks so that users are unable to download malicious files. However, after a user attempts to download a malicious file, they are still able to communicate through the SRX Series device.
Referring to the exhibit, which statement is correct?
Question 8
Which two statements are true about the configuration shown in the exhibit? (Choose two.)


Question 9
What is the correct step sequence used when Sky ATP analyzes a file?
Question 10
You are asked to implement IPS on your SRX Series device. In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)

