Question 171
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
* Users must be able to authenticate during business hours only.
* Authentication requests must be processed successfully if a single server fails.
* When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
* Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that uses password hash synchronization and seamless SSO.
The solution contains two servers that have an Authentication Agent installed.
Does this meet the goal?
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company plans to deploy several Microsoft Office 365 services.
You need to design an authentication strategy for the planned deployment. The solution must meet the following requirements:
* Users must be able to authenticate during business hours only.
* Authentication requests must be processed successfully if a single server fails.
* When the password for an on-premises user account expires, the new password must be enforced the next time the user signs in.
* Users who connect to Office 365 services from domain-joined devices that are connected to the internal network must be signed in automatically.
Solution: You design an authentication strategy that uses password hash synchronization and seamless SSO.
The solution contains two servers that have an Authentication Agent installed.
Does this meet the goal?
Question 172
You have a Microsoft 365 subscription.
You recently configured a Microsoft SharePoint Online tenant in the subscription.
You plan to create an alert policy.
You need to ensure that an alert is generated only when malware is detected in more than five documents stored in SharePoint Online during a period of 10 minutes.
What should you do first?
You recently configured a Microsoft SharePoint Online tenant in the subscription.
You plan to create an alert policy.
You need to ensure that an alert is generated only when malware is detected in more than five documents stored in SharePoint Online during a period of 10 minutes.
What should you do first?
Question 173
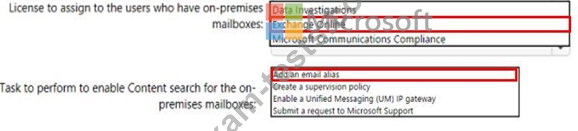
You have a Microsoft 365 E5 subscription and a hybrid deployment of Microsoft Exchange. The deployment contains TOO users who have on-premises mailboxes and 100 users who have mailboxes in Exchange Online.
You enable Microsoft Teams and assign a Microsoft Teams license to each user.
You need to ensure that the users who have on-premises mailboxes can use Microsoft Teams. All Microsoft Teams chat data must be searchable by using Content search in the Security fit Compliance admin center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You enable Microsoft Teams and assign a Microsoft Teams license to each user.
You need to ensure that the users who have on-premises mailboxes can use Microsoft Teams. All Microsoft Teams chat data must be searchable by using Content search in the Security fit Compliance admin center.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

Question 174
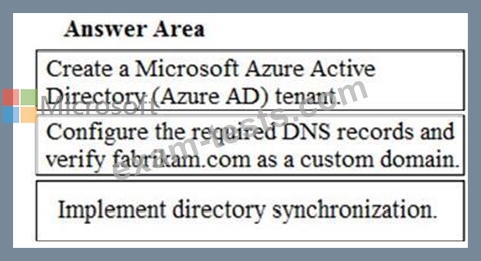
You need to prepare the environment for Project1.
You create the Microsoft 365 tenant.
Which three actions should you perform in sequence next? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You create the Microsoft 365 tenant.
Which three actions should you perform in sequence next? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

Question 175
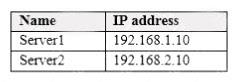
Your network contains an Active Directory domain named contoso.com. The domain contains the file servers shown in the following table.
A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 all open files that have the .abc file extension.
You implement Windows Information Protection (WIP) by using the following configurations:
* Exempt apps: App2
* Protected apps: App1
* Windows Information Protection mode: Block
* Network boundary: IPv4 range of 192.168.1.1-192.168.1.255
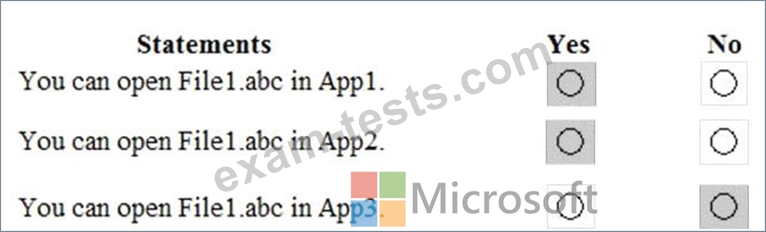
You need to identify the apps from which you can open File1.abc
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.


A file named File1.abc is stored on Server1. A file named File2.abc is stored on Server2. Three apps named App1, App2, and App3 all open files that have the .abc file extension.
You implement Windows Information Protection (WIP) by using the following configurations:
* Exempt apps: App2
* Protected apps: App1
* Windows Information Protection mode: Block
* Network boundary: IPv4 range of 192.168.1.1-192.168.1.255
You need to identify the apps from which you can open File1.abc
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.