Question 306
A network engineer is configuring wireless access for guests at an organization. Access to other areas in the organization should not be accessible to guests. Which of the following represents the MOST secure method to configure guest access to the wireless network?
Question 307
Which of the following technologies is used to attach multiple guest operating systems to a single physical network port?
Virtual switch
Virtual switch
Question 308
Joe, a user, is having issues when trying to access certain web pages. Upon navigating to a web page, it seems like it connects, but then presents the following message:
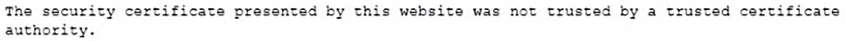
Joe has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker's desktop, but it still presented with this error.
Which of the following is the MOST likely cause of this error?

Joe has cleared his cache and cookies, rebooted his machine, and attempted to browse to the website from a coworker's desktop, but it still presented with this error.
Which of the following is the MOST likely cause of this error?
Question 309
A network technician does not have access to the GUI of a server and needs to adjust some network properties. Given the command:
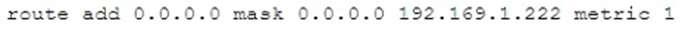
Which of the following is the technician attempting to alter?
Which of the following is the technician attempting to alter?
Question 310
A technician recently installed a new wireless access point for a SOHO with the latest wireless technologies After the installation users with older laptops report their laptops no longer show the wireless network SSID, whereas users with newer equipment do not have this issue. Which of the following is MOST likely the cause?

