Question 451
A network administrator is concerned about the management traffic between a machine and the corporate router. Which of the following protocols should the administrator use to prevent a security breach?
Question 452
Which of the following utilities would a technician use to determine the location of lost packets on a routed network?
Question 453
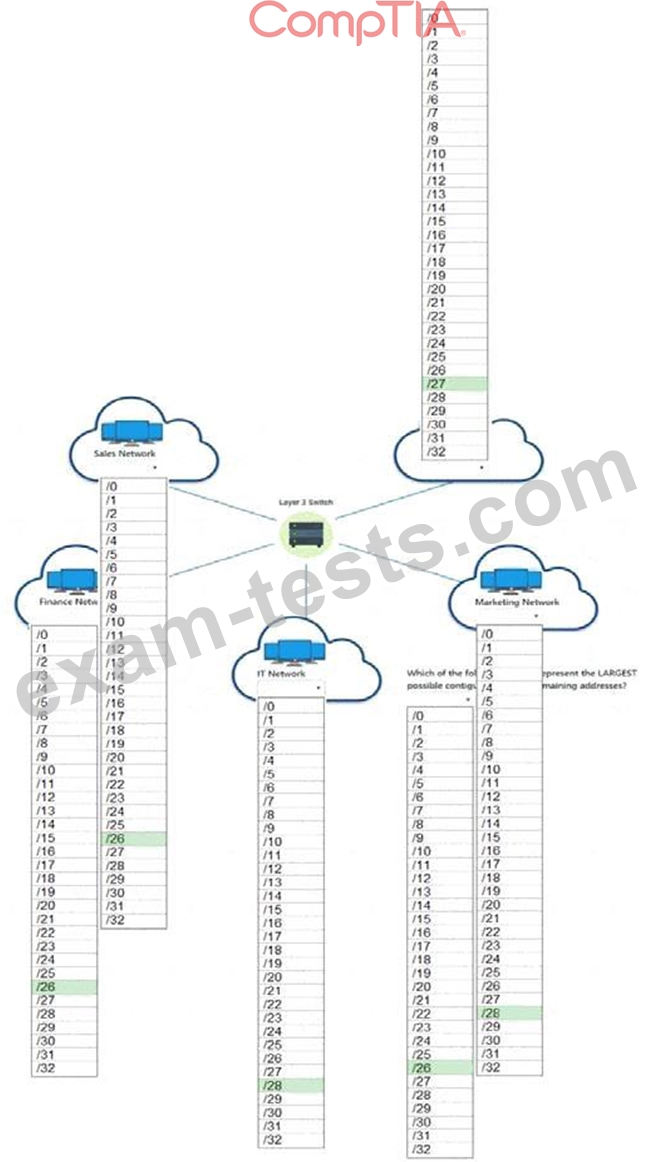
Corporate headquarters provided your office a portion of their class B subnet to use at a new office location.
Range Given: 172.30.232.0/24
* Sales 57 devices
* HR 23 devices
* IT 12 devices
* Finance 32 devices
* Marketing 9 devices
INSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
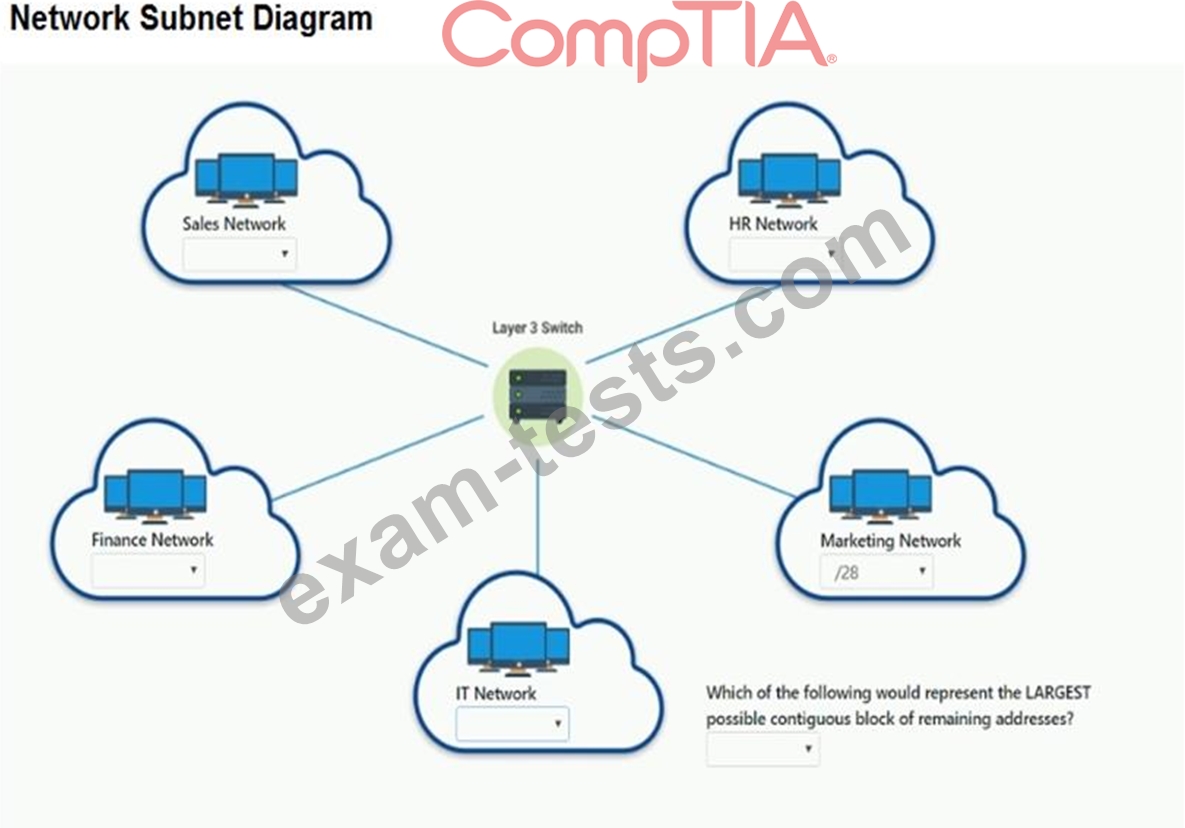

Range Given: 172.30.232.0/24
* Sales 57 devices
* HR 23 devices
* IT 12 devices
* Finance 32 devices
* Marketing 9 devices
INSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 454
The help desk is receiving reports of intermittent connections to a server. A help desk technician suspects the server is unable to establish a three-way handshake due to a DoS attack. Which of the following commands should a network administrator use to confirm the help desk technician's claim?
Question 455
A customer cannot access a company's secure website. The company's network security is reviewing the firewall for the server and finds the following output:
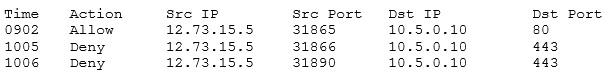
Which of the following changes should be made to allow all customers to access the company's secure website?

Which of the following changes should be made to allow all customers to access the company's secure website?