Question 86
Joe, a network technician, has received a report that one of his clients is experiencing an issue connecting to the network. Joe observes two clients are connected to a hub, which is connected to separate wall jacks.
Which of the following has MOST likely occurred?
Which of the following has MOST likely occurred?
Question 87
A network technician has finished configuring a new DHCP for a network. To ensure proper functionality, which of the following ports should be allowed on the server's local firewall? (Choose two.)
Question 88
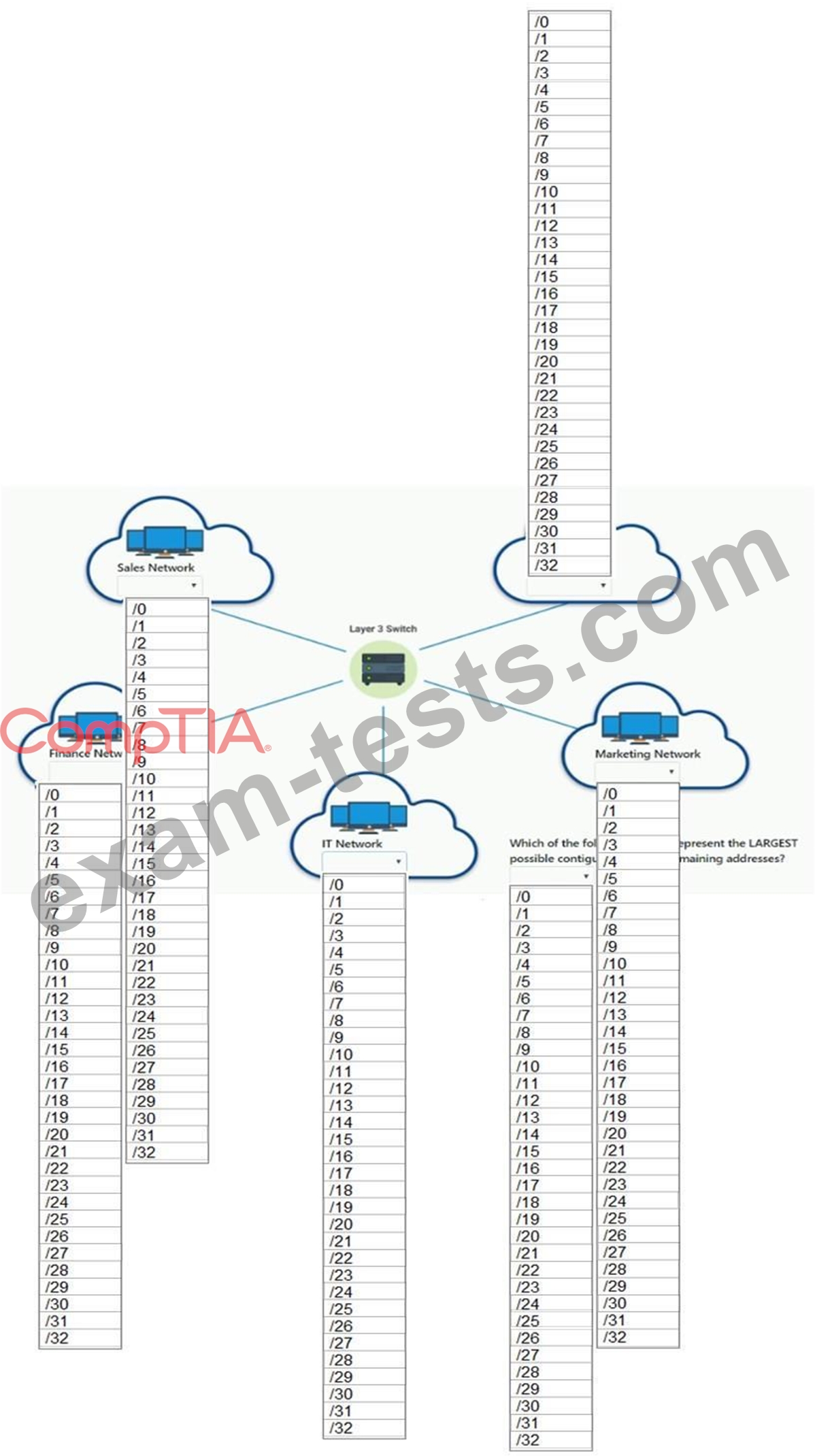
Hotspot Question
Corporate headquarters provided your office a portion of their class B subnet to use at a new office location.
Range Given: 172.30.232.0/24
* Sales 57 devices
* HR 23 devices
* IT 12 devices
* Finance 32 devices
* Marketing 9 devices
INSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Corporate headquarters provided your office a portion of their class B subnet to use at a new office location.
Range Given: 172.30.232.0/24
* Sales 57 devices
* HR 23 devices
* IT 12 devices
* Finance 32 devices
* Marketing 9 devices
INSTRUCTIONS
Allocate the minimum number of addresses (using CIDR notation) needed to accommodate each department.
After accommodating each department, identify the unused portion of the subnet by responding to the question on the graphic.
All drop downs must be filled.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 89
Your company recently purchased a new building down the street from the existing office. For each of the tasks below, select the appropriate antenna type and encryption object for all wireless access point (AP).
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation, while maximizing security.
2. Restrict the wireless signal generated by the access points (APs) inside Building 1, so that it minimizes broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1's internal wireless network is for visitors only and must not require any special configuration on the visitor's device to connect.

Instructions: When you have completed the simulation, select the Done button to submit.
1. Create an encrypted wireless connection between the two buildings that BEST controls signal propagation, while maximizing security.
2. Restrict the wireless signal generated by the access points (APs) inside Building 1, so that it minimizes broadcast beyond the building.
3. Maximize wireless coverage inside Building 1.
4. Building 1's internal wireless network is for visitors only and must not require any special configuration on the visitor's device to connect.

Instructions: When you have completed the simulation, select the Done button to submit.
Question 90
An administrator recently implemented new SOHO routers for a company's teleworking employees. Before deploying the routers, the administrator changed the default credentials and disabled unnecessary services. Within a few days of deployment, hackers gained access to the routers. Which of the following is the MOST important thing the administrator forgot to do?



