Question 51
Refer to the exhibit showing a FortiSOAR playbook.
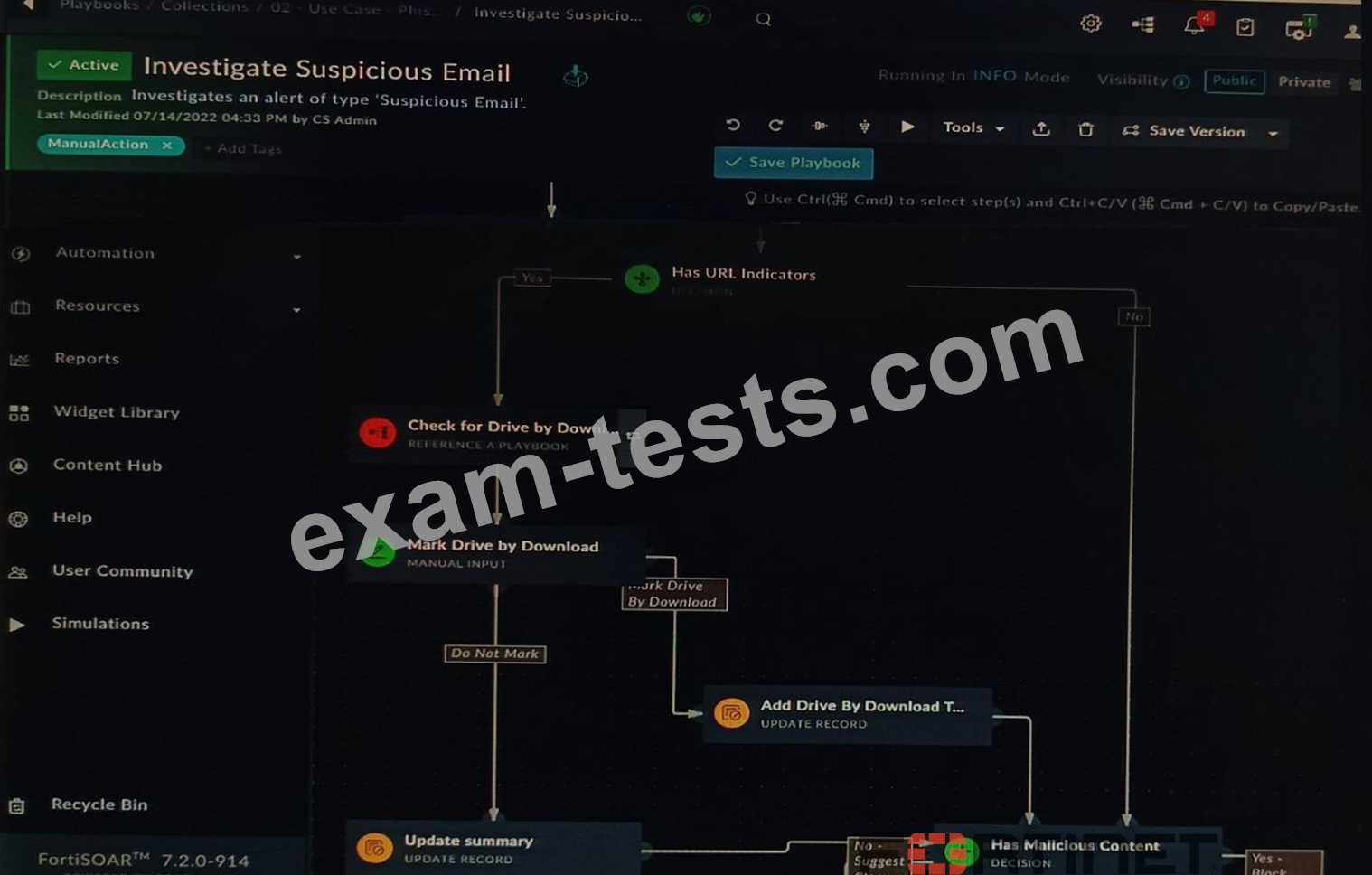
You are investigating a suspicious e-mail alert on FortiSOAR, and after reviewing the executed playbook, you can see that it requires intervention.
What should be your next step?

You are investigating a suspicious e-mail alert on FortiSOAR, and after reviewing the executed playbook, you can see that it requires intervention.
What should be your next step?
Question 52
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
Question 53
Refer to The exhibit, which shows a topology diagram.
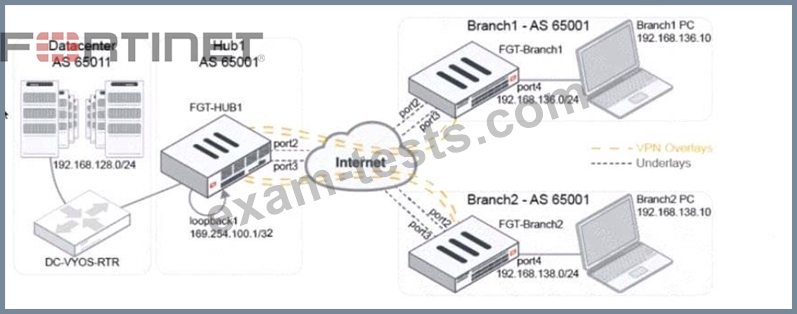
A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?

A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?
Question 54
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
Question 55
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network.
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?

