Question 61
Refer to the exhibits.
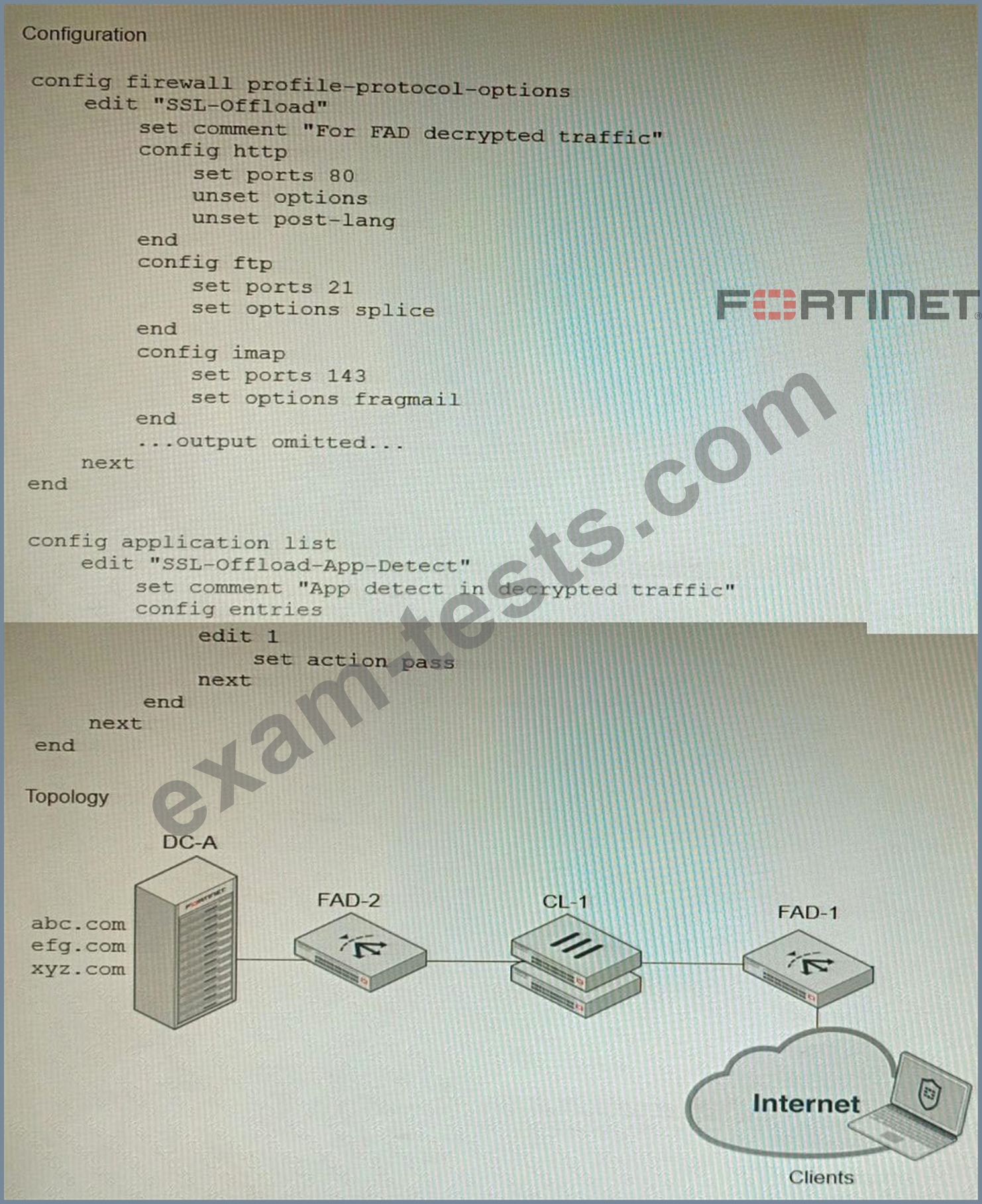
A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)

A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
Question 62
Refer to the exhibits.
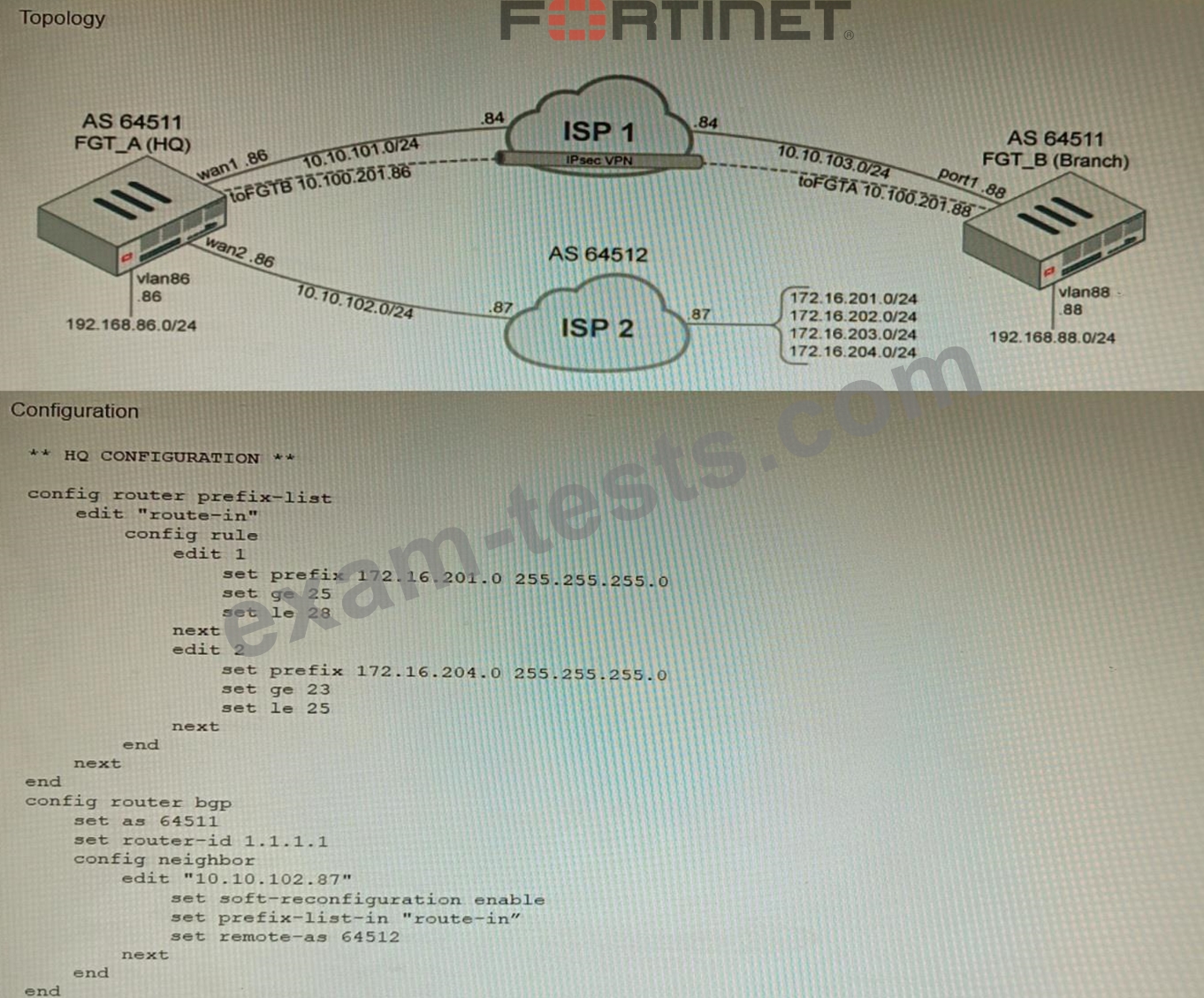
A customer has deployed a FortiGate with iBGP and eBGP routing enabled. HQ is receiving routes over eBGP from ISP 2; however, only certain routes are showing up in the routing table-Assume that BGP is working perfectly and that the only possible modifications to the routing table are solely due to the prefix list that is applied on HQ.
Given the exhibits, which two routes will be active in the routing table on the HQ firewall? (Choose two.)

A customer has deployed a FortiGate with iBGP and eBGP routing enabled. HQ is receiving routes over eBGP from ISP 2; however, only certain routes are showing up in the routing table-Assume that BGP is working perfectly and that the only possible modifications to the routing table are solely due to the prefix list that is applied on HQ.
Given the exhibits, which two routes will be active in the routing table on the HQ firewall? (Choose two.)
Question 63
Refer to the exhibit.
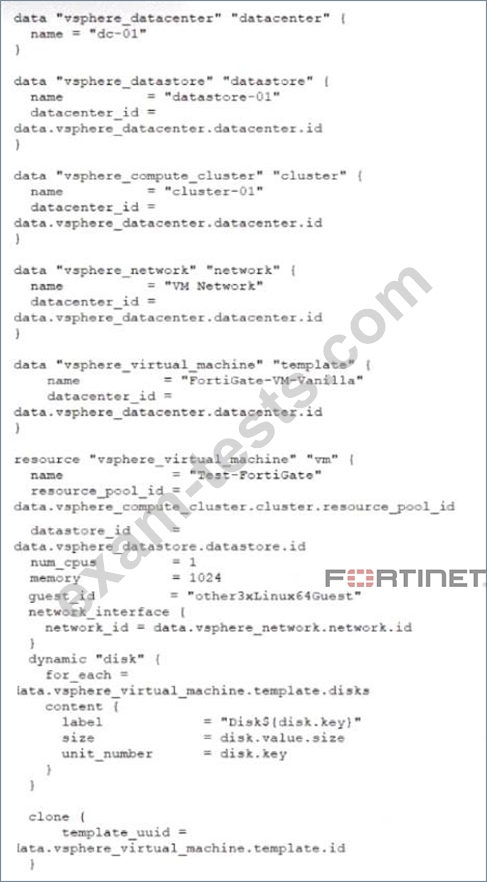
A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?

A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?
Question 64
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
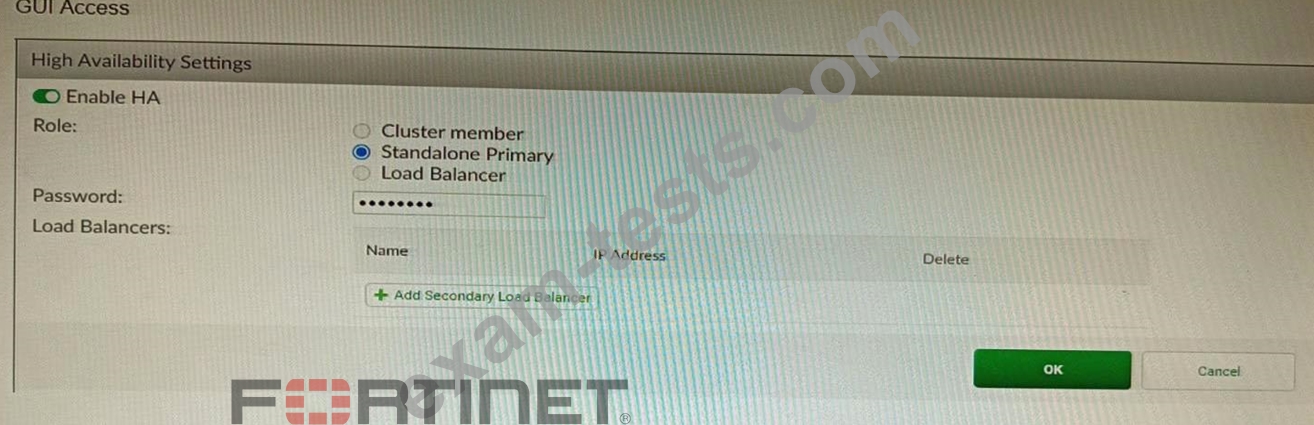
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?

Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
Question 65
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)

