Question 11
A customer wants to scan a serverless function as part of a build process.
Which twistcli command can be used to scan serverless functions?
Which twistcli command can be used to scan serverless functions?
Question 12
Which three types of buckets exposure are available in the Data Security module? (Choose three.)
Question 13
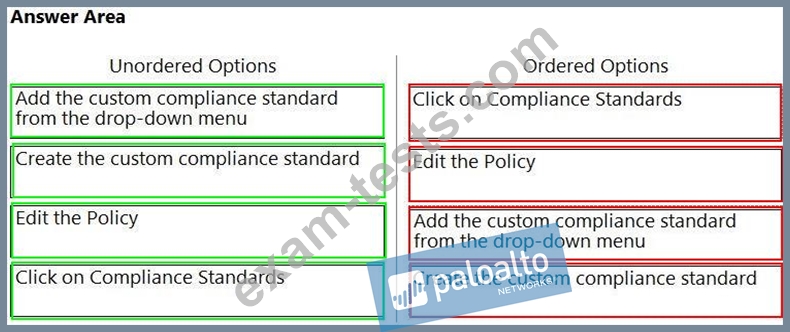
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
(Drag the steps into the correct order of occurrence, from the first step to the last.)

Question 14
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise.
tenant-In which order will the APIs be executed for this service? (Drag the steps into the correct order of occurrence from the first step to the last)

tenant-In which order will the APIs be executed for this service? (Drag the steps into the correct order of occurrence from the first step to the last)

Question 15
An administrator sees that a runtime audit has been generated for a Container The audit message is DNS resolution of suspicious name wikipedia.com. type A".
Why would this message appear as an audit?
Why would this message appear as an audit?