Question 16
Review this admission control policy:
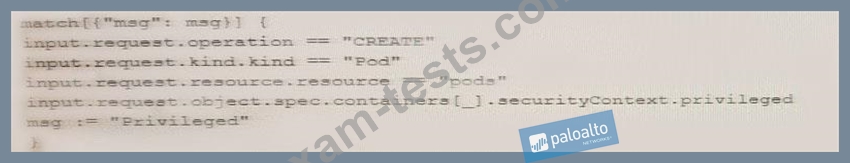
Which response to this policy will be achieved when the effect is set to "block"?

Which response to this policy will be achieved when the effect is set to "block"?
Question 17
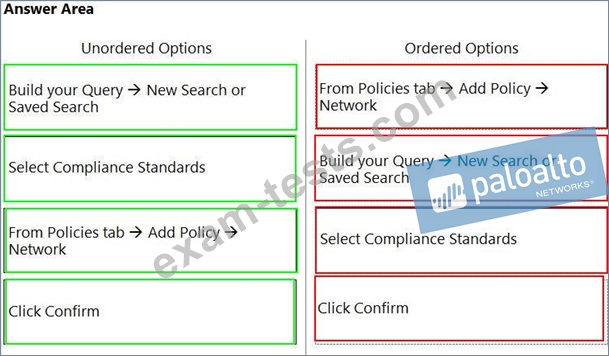
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
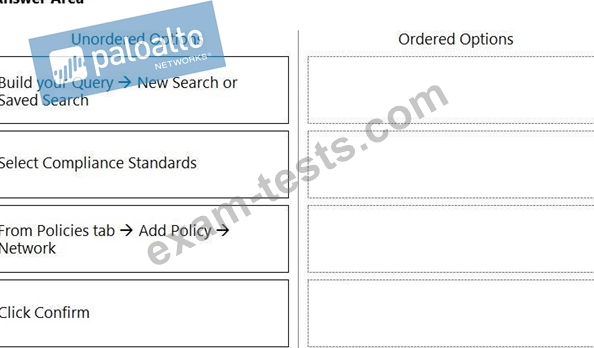
(Drag the steps into the correct order of occurrence, from the first step to the last.)

Question 18
Which options show the steps required after upgrade of Console?
Question 19
The security team wants to protect a web application container from an SQLi attack? Which type of policy should the administrator create to protect the container?
Question 20
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?