Question 81
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
Question 82
Given the following RQL:
event from cloud.audit_logs where operation IN ('CreateCryptoKey', 'DestroyCryptoKeyVersion',
'v1.compute.disks.createSnapshot')
Which audit event snippet is identified?
A)
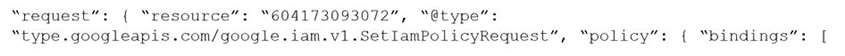
B)

C)
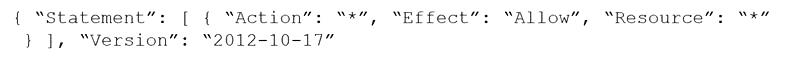
D)

event from cloud.audit_logs where operation IN ('CreateCryptoKey', 'DestroyCryptoKeyVersion',
'v1.compute.disks.createSnapshot')
Which audit event snippet is identified?
A)
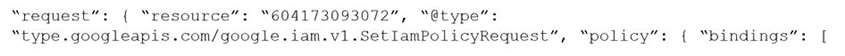
B)

C)
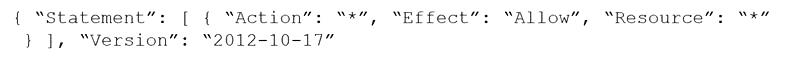
D)

Question 83
A security team notices a number of anomalies under Monitor > Events The incident response team works with the developers to determine that these anomalies are false positives.
What will be the effect if the security team chooses to Relearn on this image?
What will be the effect if the security team chooses to Relearn on this image?
Question 84
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
Question 85
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
Which port should the team specify in the CNAF rule to protect the application?

