Question 51
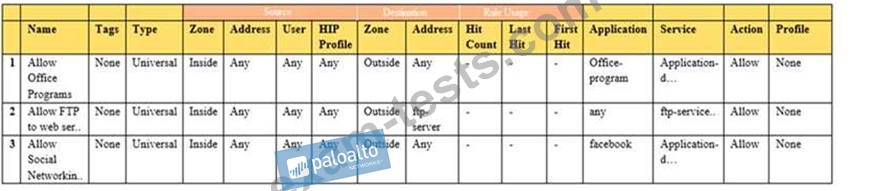
Given the image, which two options are true about the Security policy rules. (Choose two.)

Question 52
Which solution is a viable option to capture user identification when Active Directory is not in use?
Question 53
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic Which statement accurately describes how the firewall will apply an action to matching traffic?
Question 54
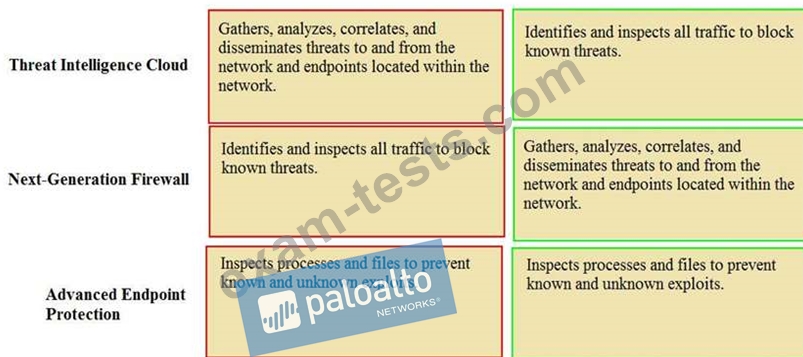
Match the Palo Alto Networks Security Operating Platform architecture to its description.


Question 55
Match the Palo Alto Networks Security Operating Platform architecture to its description.