Question 56
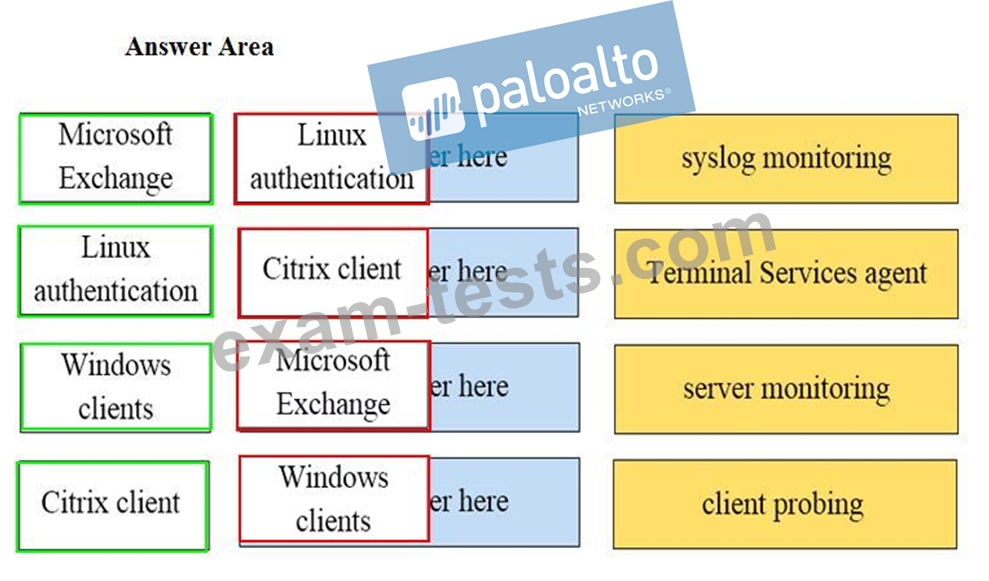
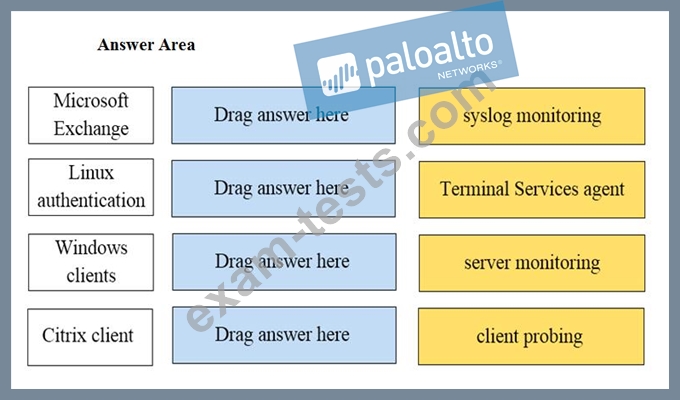
Match the network device with the correct User-ID technology.

Question 57
Which statement is true regarding a Best Practice Assessment?
Question 58
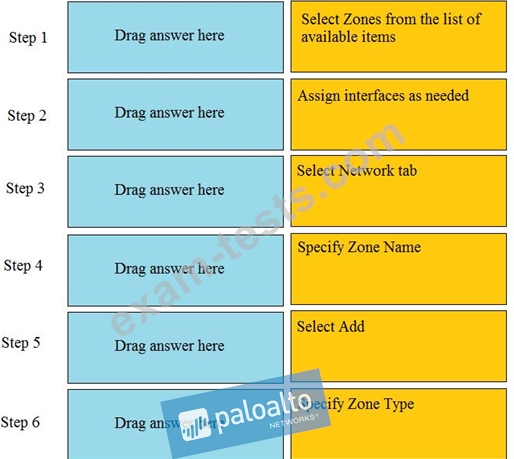
Order the steps needed to create a new security zone with a Palo Alto Networks firewall.

Question 59
Which type firewall configuration contains in-progress configuration changes?
Question 60
Refer to the exhibit. An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and Host B (10.1.1.101) receives SSH traffic.

Which two Security policy rules will accomplish this configuration? (Choose two.)

Which two Security policy rules will accomplish this configuration? (Choose two.)