Question 106
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
Question 107
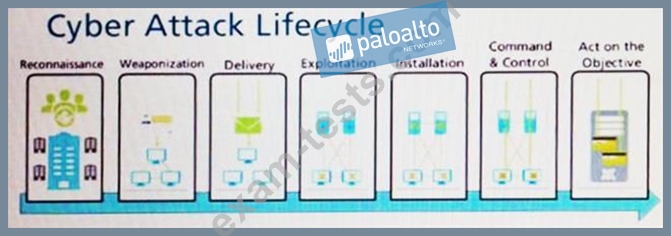
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.

Question 108
Which two statements are true for the DNS security service introduced in PAN-OS version 9.0?
Question 109
Which data-plane processor layer of the graphic shown provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall?


Question 110
Which statement is true regarding a Heatmap report?
Premium Bundle
Newest PCNSA Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PCNSA Exam! BraindumpsPass.com now offer the updated PCNSA exam dumps, the BraindumpsPass.com PCNSA exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PCNSA pdf dumps with Exam Engine here:

