Question 121
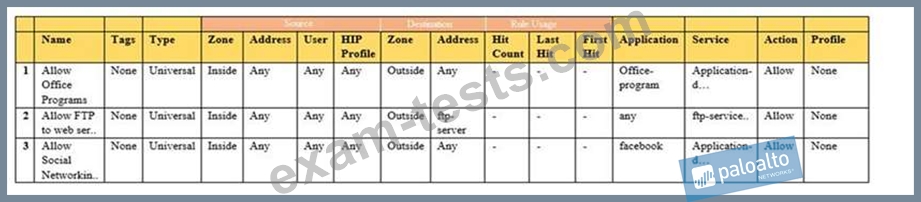
Given the image, which two options are true about the Security policy rules. (Choose two.)

Question 122
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
Question 123
Access to which feature requires the PAN-OS Filtering license?
Question 124
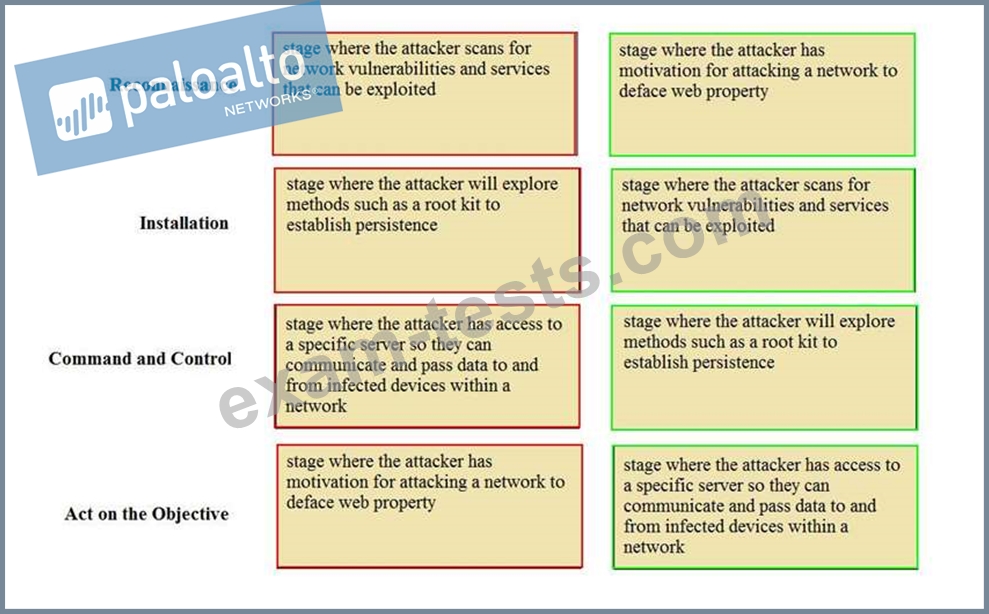
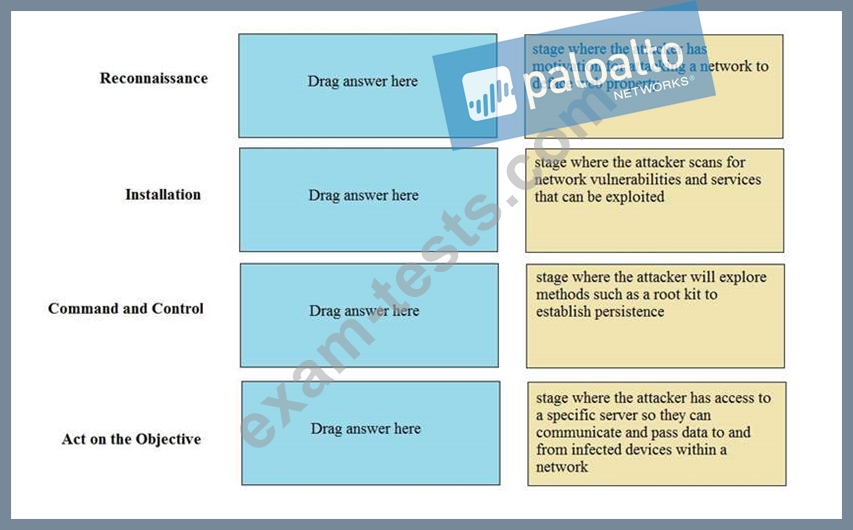
Match the Cyber-Attack Lifecycle stage to its correct description.

Question 125
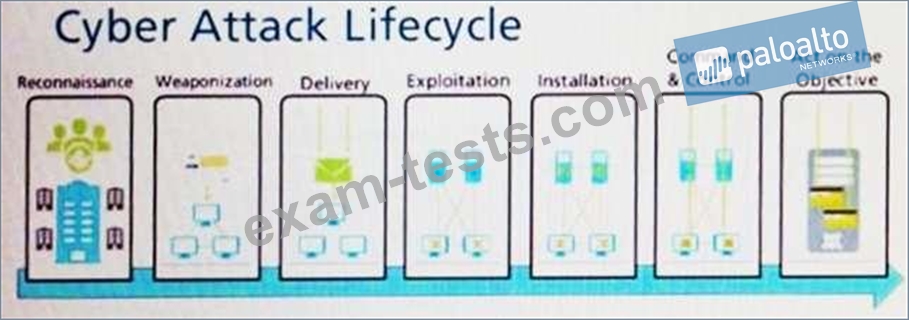
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.