Question 181
When performing compliance-based assessments, which of the following is the MOST important Key consideration?
Question 182
Click the exhibit button.
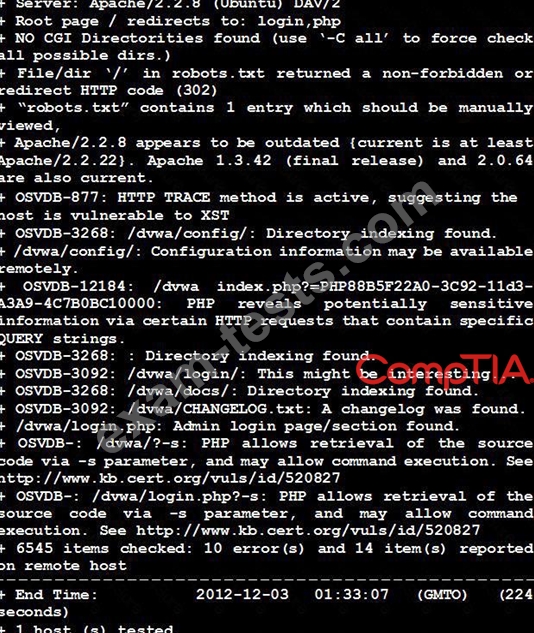
Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)

Given the Nikto vulnerability, scan output shown in the exhibit, which of the following exploitation techniques might be used to exploit the target system? (Choose two.)
Question 183
When communicating the findings of a network vulnerability scan to a client's IT department which of the following metrics BEST prioritize the severity of the findings? (Select TWO)
Question 184
A company received a report with the following finding
While on the internal network the penetration tester was able to successfully capture SMB broadcasted user ID and password information on the network and decode this information This allowed the penetration tester to then join their own computer to the ABC domain Which of the following remediation's are appropriate for the reported findings'? (Select TWO)
While on the internal network the penetration tester was able to successfully capture SMB broadcasted user ID and password information on the network and decode this information This allowed the penetration tester to then join their own computer to the ABC domain Which of the following remediation's are appropriate for the reported findings'? (Select TWO)
Question 185
A penetration tester directly connects to an internal network. Which of the following exploits would work BEST for quick lateral movement within an internal network?
Premium Bundle
Newest PT0-001 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-001 Exam! BraindumpsPass.com now offer the updated PT0-001 exam dumps, the BraindumpsPass.com PT0-001 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-001 pdf dumps with Exam Engine here:

