Question 191
Joe a penetration tester, was able to exploit a web application behind a firewall He is trying to get a reverse shell back to his machine but the firewall blocks the outgoing traffic Ports for which of the following should the security consultant use to have the HIGHEST chance to bypass the firewall?
Question 192
After successfully enumerating users on an Active Directory domain controller using enum4linux a penetration tester wants to conduct a password-guessing attack Given the below output:
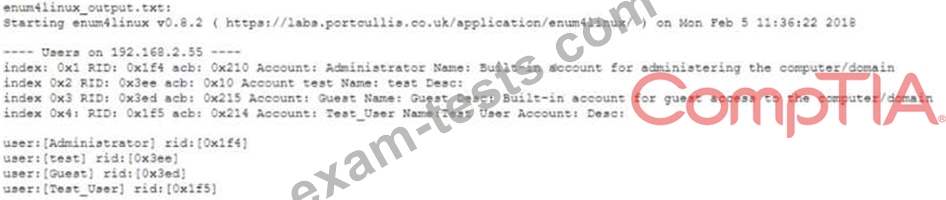
Which of the following can be used to extract usernames from the above output prior to conducting the attack?

Which of the following can be used to extract usernames from the above output prior to conducting the attack?
Question 193
A software development team recently migrated to new application software on the on-premises environment Penetration test findings show that multiple vulnerabilities exist If a penetration tester does not have access to a live or test environment, a test might be better to create the same environment on the VM Which of the following is MOST important for confirmation?
Question 194
A penetration tester calls human resources and begins asking open-ended questions Which of the following social engineering techniques is the penetration tester using?
Question 195
Which of the following tools is used to perform a credential brute force attack?

