Question 26
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
Question 27
An Nmap scan shows open ports on web servers and databases. A penetration tester decides to run WPScan and SQLmap to identify vulnerabilities and additional information about those systems.
Which of the following is the penetration tester trying to accomplish?
Which of the following is the penetration tester trying to accomplish?
Question 28
Which of the following tools provides Python classes for interacting with network protocols?
Question 29
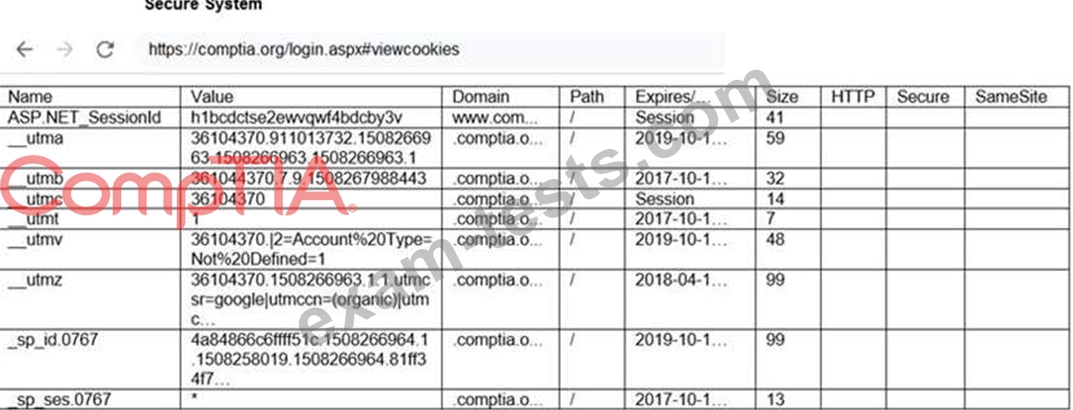
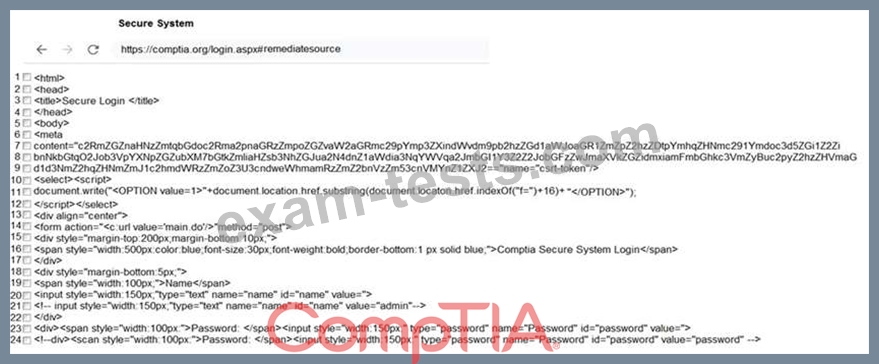
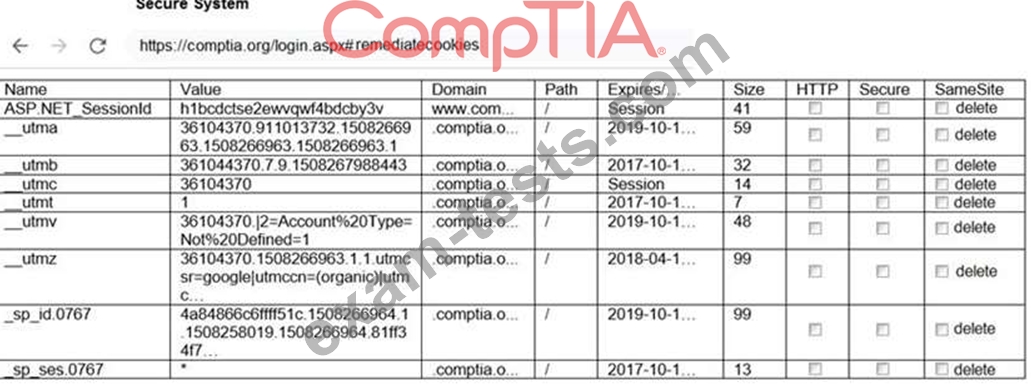
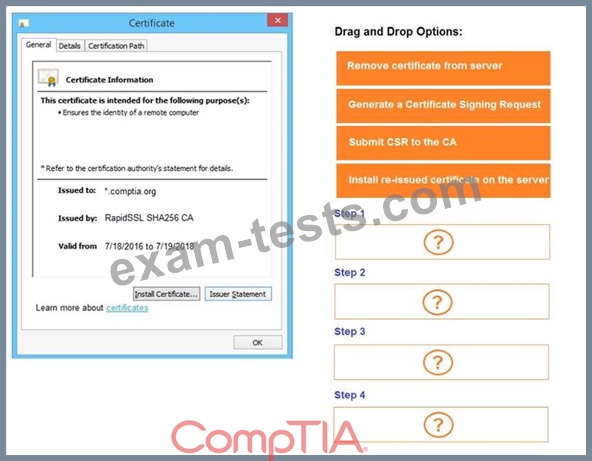
You are a penetration tester reviewing a client's website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
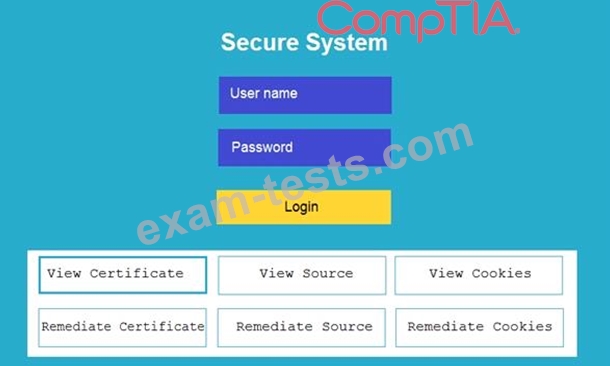
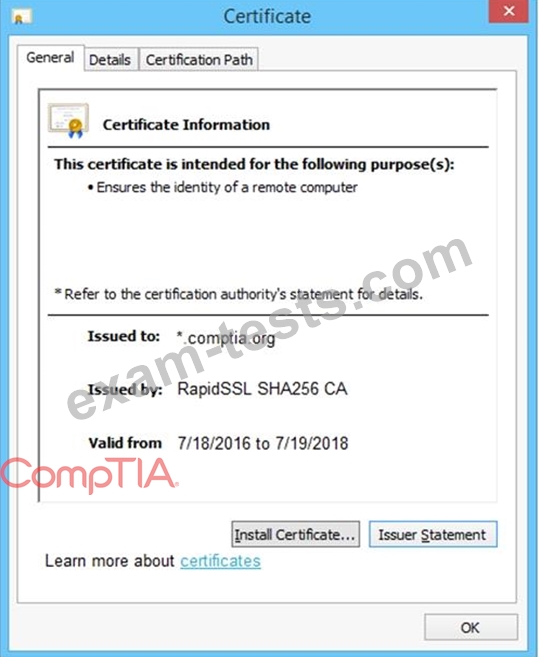
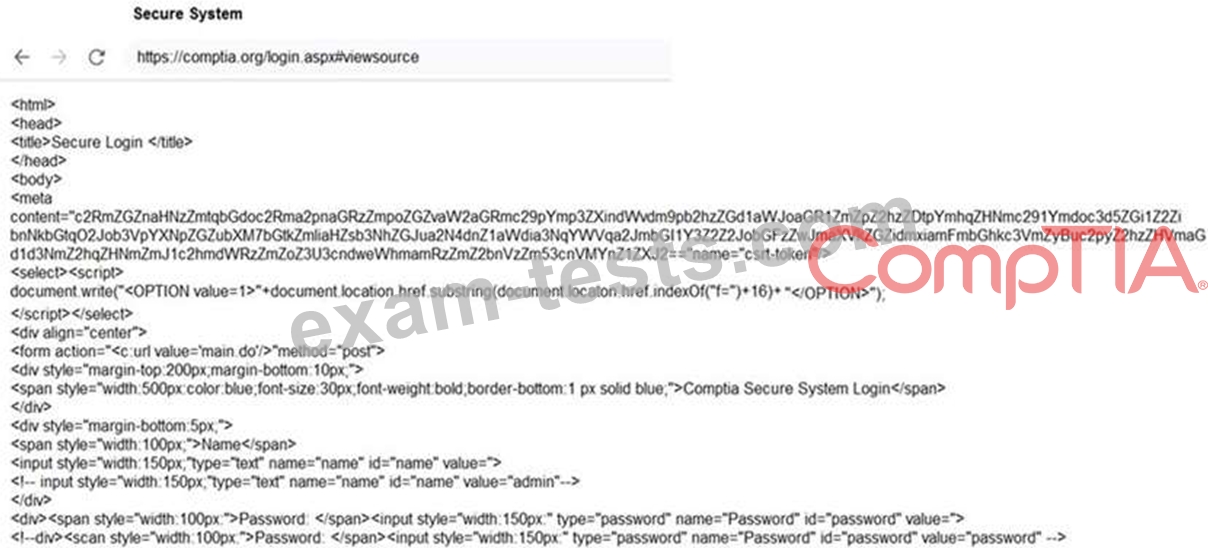
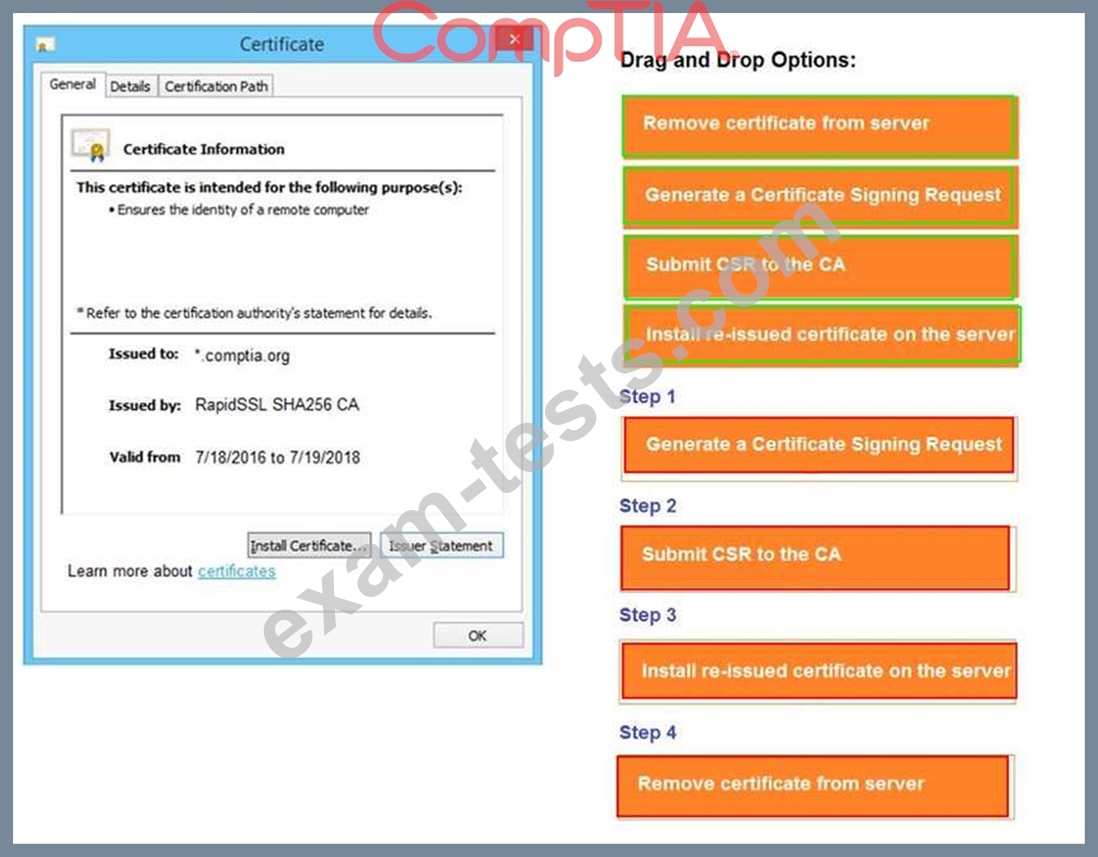
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.







Question 30
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62 Which of the following commands can be used to further attack the website?
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62 Which of the following commands can be used to further attack the website?
Premium Bundle
Newest PT0-002 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing PT0-002 Exam! BraindumpsPass.com now offer the updated PT0-002 exam dumps, the BraindumpsPass.com PT0-002 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com PT0-002 pdf dumps with Exam Engine here: