Question 46
A penetration tester performs the following command:
curl -I -http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
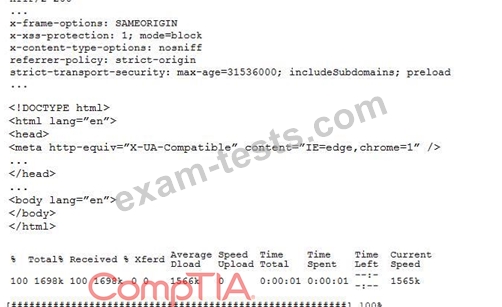
curl -I -http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?

Question 47
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
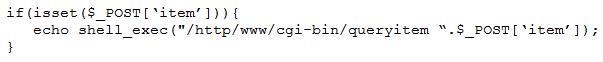
Which of the following tools will help the tester prepare an attack for this scenario?

Which of the following tools will help the tester prepare an attack for this scenario?
Question 48
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Have a full TCP connection
Send a "hello" payload
Walt for a response
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
Have a full TCP connection
Send a "hello" payload
Walt for a response
Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
Question 49
A penetration tester is working on a scoping document with a new client. The methodology the client uses includes the following:
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
Pre-engagement interaction (scoping and ROE)
Intelligence gathering (reconnaissance)
Threat modeling
Vulnerability analysis
Exploitation and post exploitation
Reporting
Which of the following methodologies does the client use?
Question 50
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company's web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)

