Question 16
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.

You have a retention policy that has the following configurations:
Name: Policy1
Retain items for a specific period: 5 years
Locations to apply the policy: Exchange email, SharePoint sites
You place a Preservation Lock on Policy1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.


You have a retention policy that has the following configurations:
Name: Policy1
Retain items for a specific period: 5 years
Locations to apply the policy: Exchange email, SharePoint sites
You place a Preservation Lock on Policy1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Question 17
You have a data loss prevention (DLP) policy that applies to the Devices location. The policy protects documents that contain States passport numbers.
Users reports that they cannot upload documents to a travel management website because of the policy.
You need to ensure that the users can upload the documents to the travel management website. The solution must prevent the protected content from being uploaded to other locations.
Which Microsoft 365 Endpoint data loss prevention (Endpoint DLP) setting should you configure?
Users reports that they cannot upload documents to a travel management website because of the policy.
You need to ensure that the users can upload the documents to the travel management website. The solution must prevent the protected content from being uploaded to other locations.
Which Microsoft 365 Endpoint data loss prevention (Endpoint DLP) setting should you configure?
Question 18
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You onboard the computers to Microsoft Defender for Endpoint.
Does this meet the goal?
Question 19
You have a Microsoft 365 tenant that uses records management.
You use a retention label to mark legal files stored in a Microsoft SharePoint Online document library as regulatory records.
What can you do to the legal files?
You use a retention label to mark legal files stored in a Microsoft SharePoint Online document library as regulatory records.
What can you do to the legal files?
Question 20
You have a Microsoft 365 tenant that uses trainable classifiers.
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.
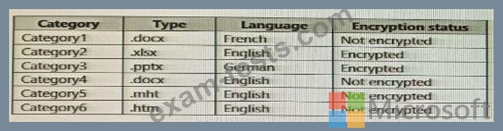
Which file categories can be used as seed content?
You are creating a custom trainable classifier.
You collect 300 sample file types from various geographical locations to use as seed content. Some of the file samples are encrypted.
You organize the files into categories as shown in the following table.

Which file categories can be used as seed content?


