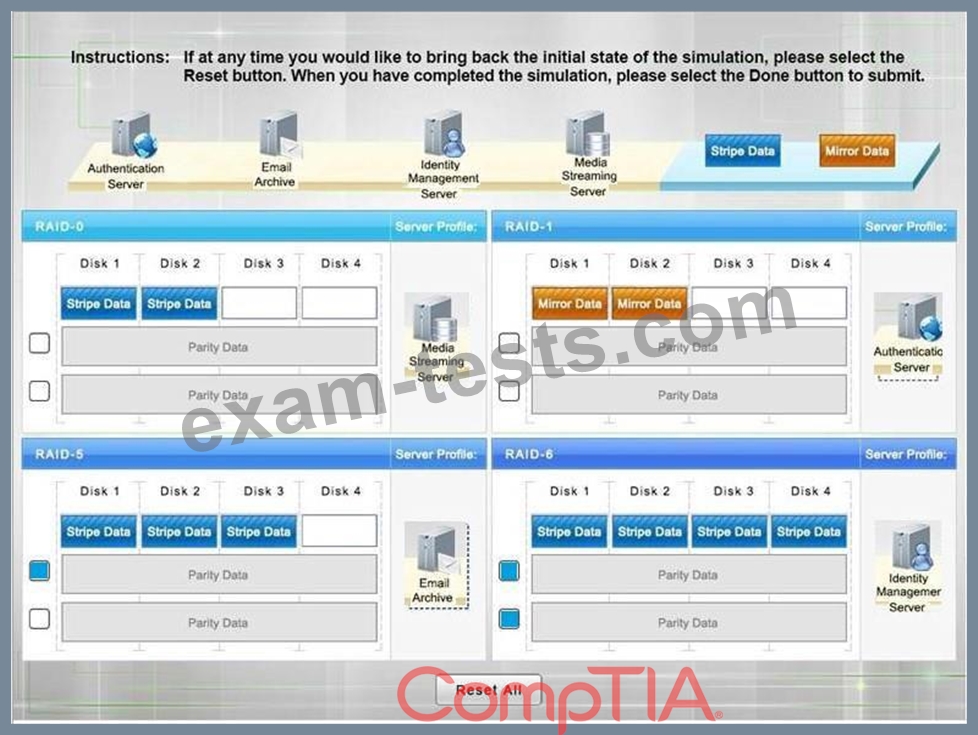
Question 241
A security administrator is given the security and availability profiles for servers that are being deployed.
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 242
A new intern in the purchasing department requires read access to shared documents.
Permissions are normally controlled through a group called "Purchasing", however, the purchasing group permissions allow write access.
Which of the following would be the BEST course of action?
Permissions are normally controlled through a group called "Purchasing", however, the purchasing group permissions allow write access.
Which of the following would be the BEST course of action?
Question 243
When connected to a secure WAP, which of the following encryption technologies is MOST likely to be configured when connecting to WPA2-PSK?
Question 244
Which of the following is a security consideration for IoT devices?
Question 245
A security analyst captures forensic evidence from a potentially compromised system for further investigation.
The evidence is documented and securely stored to FIRST:
The evidence is documented and securely stored to FIRST: