Question 481
Phishing emails frequently take advantage of high-profile catastrophes reported in the news. Which of the following principles BEST describes the weakness being exploited?
Question 482
A company just implemented a new telework policy that allows employees to use personal devices for official email and file sharing while working from home. Some of the requirements are:
* Employees must provide an alternate work location (i.e., a home address).
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
* Employees must provide an alternate work location (i.e., a home address).
* Employees must install software on the device that will prevent the loss of proprietary data but will not restrict any other software from being installed.
Which of the following BEST describes the MDM options the company is using?
Question 483
An analyst has determined that a server was not patched and an external actor extiltrated data on port 139. Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?
Question 484
Joe, an employee, wants to show his colleagues how much he knows about smartphones. Joe demonstrates a free movie application that he installed from a third party on his corporate smartphone. Joe's colleagues were unable to find the application in the app stores. Which of the following allowed Joe to install the application? (Select two.)
Question 485
A security administrator is reviewing the following firewall configuration after receiving reports that users are unable to connect to remote websites:
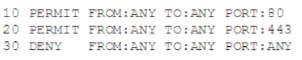
Which of the following is the MOST secure solution the security administrator can implement to fix this issue?

Which of the following is the MOST secure solution the security administrator can implement to fix this issue?


