Question 41
Which of the following is an example of risk avoidance?
Question 42
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
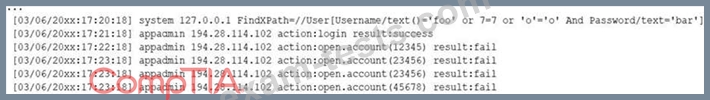
Which of the following can the security analyst conclude?

Which of the following can the security analyst conclude?
Question 43
A security analyst is reviewing the following attack log output:
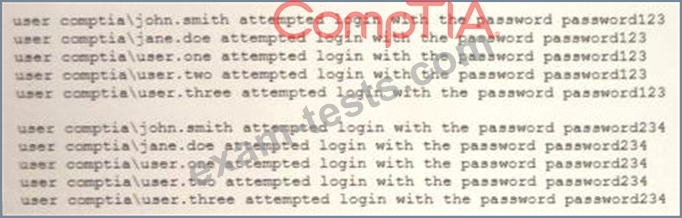
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?
Question 44
An organization's RPO for a critical system is two hours. The system is used Monday through Friday, from 9:00 am to 5:00 pm. Currently, the organization performs a full backup every Saturday that takes four hours to complete. Which of the following additional backup implementations would be the BEST way for the analyst to meet the business requirements?
Question 45
Employees are having issues accessing the company's website. Some employees report very slow performance, while others cannot the website at all. The web and security administrators search the logs and find millions of half-open connections to port 443 on the web server. Further analysis reveals thousands of different source IPs initiating this traffic. Which of the following attacks is MOST likely occurring?

