Question 36
Joe, a user at a company, clicked an email link led to a website that infected his workstation. Joe, was connected to the network, and the virus spread to the network shares. The protective measures failed to stop this virus, and It has continues to evade detection. Which of the following should administrator implement to protect the environment from this malware?
Question 37
A security analyst needs to be proactive in understanding the types of attacks that could potentially target the company's executives. Which of the following intelligence sources should the security analyst review?
Question 38
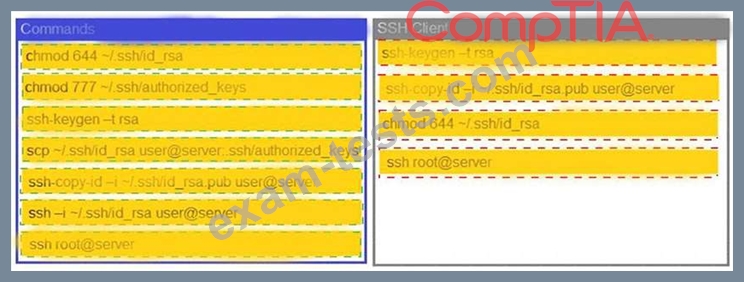
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 39
A security engineer needs to implement an MDM solution that complies with the corporate mobile device policy.
The policy states that in order for mobile users to access corporate resources on their devices the following requirements must be met:
* Mobile device OSs must be patched up to the latest release
* A screen lock must be enabled (passcode or biometric)
* Corporate data must be removed if the device is reported lost or stolen
Which of the following controls should the security engineer configure? (Select TWO)
The policy states that in order for mobile users to access corporate resources on their devices the following requirements must be met:
* Mobile device OSs must be patched up to the latest release
* A screen lock must be enabled (passcode or biometric)
* Corporate data must be removed if the device is reported lost or stolen
Which of the following controls should the security engineer configure? (Select TWO)
Question 40
Which of the following would BEST identify and remediate a data-loss event in an enterprise using third-party, web-based services and file-sharing platforms?