Question 111
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:
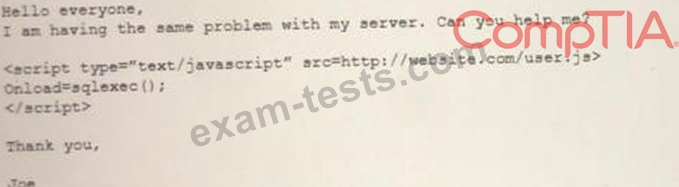
Which of the following BEST describes the attack that was attempted against the forum readers?

Which of the following BEST describes the attack that was attempted against the forum readers?
Question 112
An organization is developing an authentication service for use at the entry and exit ports of country borders. The service will use data feeds obtained from passport systems, passenger manifests, and high-definition video feeds from CCTV systems that are located at the ports. The service will incorporate machine-learning techniques to eliminate biometric enrollment processes while still allowing authorities to identify passengers with increasing accuracy over time. The more frequently passengers travel, the more accurately the service will identify them. Which of the following biometrics will MOST likely be used, without the need for enrollment? (Choose two.)
Question 113
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
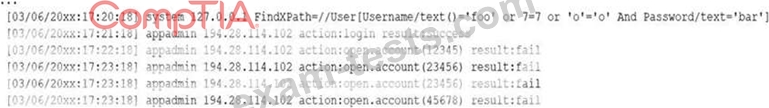
Which of the following can the security analyst conclude?

Which of the following can the security analyst conclude?
Question 114
An end user reports a computer has been acting slower than normal for a few weeks, During an investigation, an analyst determines the system 3 sending the users email address and a ten-digit number ta an IP address once a day. The only resent log entry regarding the user's computer is the following:

Which of the following is the MOST likely cause of the issue?

Which of the following is the MOST likely cause of the issue?
Question 115
A security analyst sees the following log output while reviewing web logs:

Which of the following mitigation strategies would be BEST to prevent this attack from being successful?

Which of the following mitigation strategies would be BEST to prevent this attack from being successful?

