Question 116
A Chief Information Security Officer (CISO) needs to create a policy set that meets international standards for data privacy and sharing. Which of the following should the CISO read and understand before writing the policies?
Question 117
Which of the following would MOST likely support the integrity of a voting machine?
Question 118
A manufacturing company has several one-off legacy information systems that cannot be migrated to a newer OS due to software compatibility issues. The Oss are still supported by the vendor, but the industrial software is no longer supported. The Chief Information Security Officer (CISO) has created a resiliency plan for these systems that will allow OS patches to be installed in a non-production environment, while also creating backups of the systems for recovery. Which of the following resiliency techniques will provide these capabilities?
Question 119
A security analyst is reviewing the following command-line output:
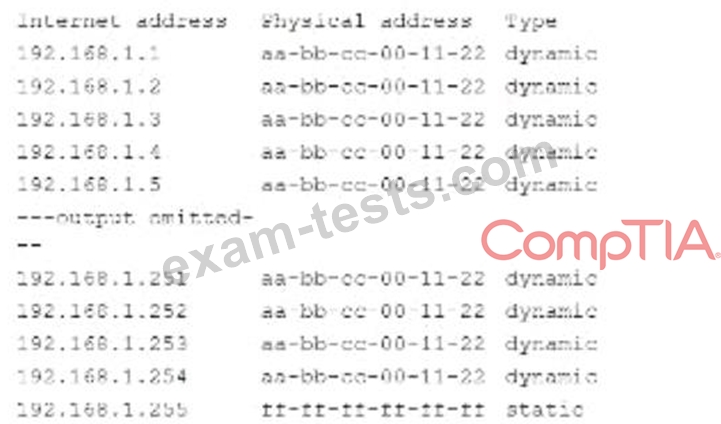
Which of the following Is the analyst observing?

Which of the following Is the analyst observing?
Question 120
A nationwide company is experiencing unauthorized logins at all hours of the day.
The logins appear to originate from countries in which the company has no employees. Which of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).
The logins appear to originate from countries in which the company has no employees. Which of the following controls.
should the company consider using as part of its IAM strategy? (Select TWO).

