Question 151
A malicious actor recently penetration a company's network and moved laterally to the datacenter. Upon investigation, a forensics firm wants to know was in the memory on the compromised server. Which of the following files should be given to the forensics firm?
Question 152
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst MOST likely seeing?
A)
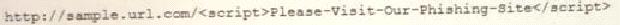
B)
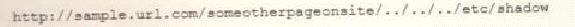
C)
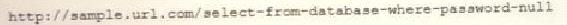
D)
A)
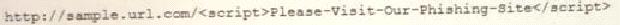
B)
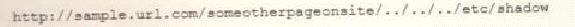
C)
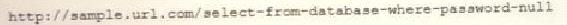
D)
Question 153
Which of the following is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?
Question 154
Which of the following terms should be included in a contract to help a company monitor the ongoing security maturity of a new vendor?
Question 155
A company's Chief Information Security Officer (CISO) recently warned the security manager that the company's Chief Executive Officer (CEO) is planning to publish a controversial option article in a national newspaper, which may result in new cyberattacks Which of the following would be BEST for the security manager to use in a threat mode?

