Question 176
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
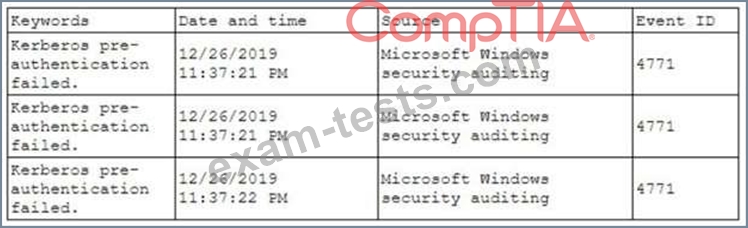
To better understand what is going on, the analyst runs a command and receives the following output:
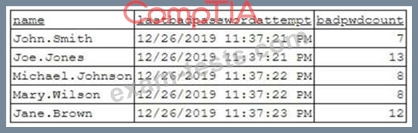
Based on the analyst's findings, which of the following attacks is being executed?

To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?
Question 177
A recent audit uncovered a key finding regarding the use of a specific encryption standard in a web application that is used to communicate with business customers. Due to the technical limitations of its customers the company is unable to upgrade the encryption standard. Which of the following types of controls should be used to reduce the risk created by this scenario?
Question 178
The
website http://companywebsite.com requires users to provide personal information including security responses, for registration. which of the following would MOST likely cause a date breach?
website http://companywebsite.com requires users to provide personal information including security responses, for registration. which of the following would MOST likely cause a date breach?
Question 179
A external forensics investigator has been hired to investigate a data breach at a large enterprise with numerous assets. It is known that the breach started in the DMZ and moved to the sensitive information, generating multiple logs as the attacker traversed through the network. Which of the following will BEST assist with this investigation?
Question 180
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:

Which of the following BEST describes the attack that was attempted against the forum readers?

Which of the following BEST describes the attack that was attempted against the forum readers?

