Question 356
A security analyst needs to determine how an attacker was able to use User3 to gain a foothold within a company's network. The company's lockout policy requires that an account be locked out for a minimum of 15 minutes after three unsuccessful attempts. While reviewing the log files, the analyst discovers the following:
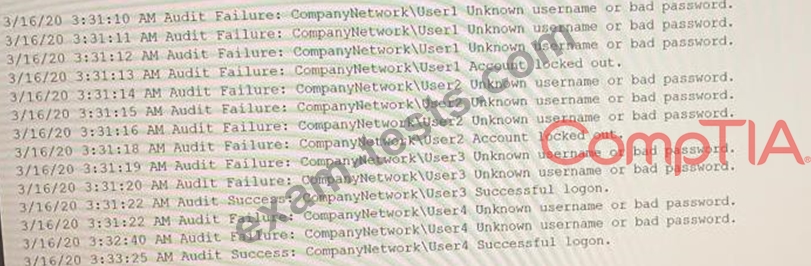
Which of the following attacks MOST likely occurred?

Which of the following attacks MOST likely occurred?
Question 357
During a security assessment, a security finds a file with overly permissive permissions. Which of the following tools will allow the analyst to reduce the permission for the existing users and groups and remove the set-user-ID from the file?
Question 358
An end user reports a computer has been acting slower than normal for a few weeks. During an investigation, an analyst determines the system is sending the user's email address and a ten-digit number to an IP address once a day. The only recent log entry regarding the user's computer is the following:

Which of the following is the MOST likely cause of the issue?

Which of the following is the MOST likely cause of the issue?
Question 359
A forensics examiner is attempting to dump password cached in the physical memory of a live system but keeps receiving an error message. Which of the following BEST describes the cause of the error?
Question 360
After a phishing scam for a user's credentials, the red team was able to craft a payload to deploy on a server.
The attack allowed the installation of malicious software that initiates a new remote session. Which of the following types of attacks has occurred?
The attack allowed the installation of malicious software that initiates a new remote session. Which of the following types of attacks has occurred?

