Question 336
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
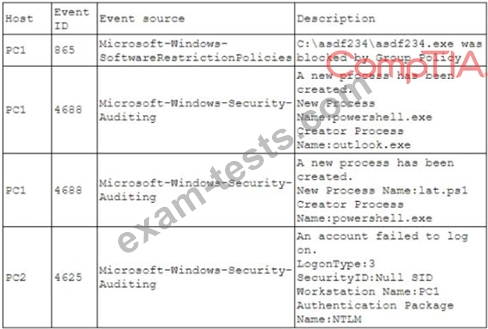
Which of the following describes the method that was used to compromise the laptop?

Which of the following describes the method that was used to compromise the laptop?
Question 337
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company's data?
Question 338
Given the following logs:
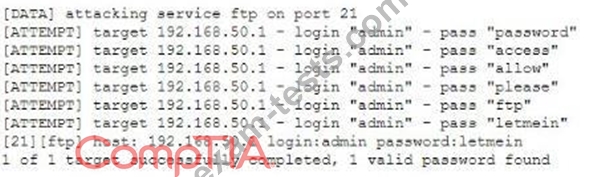
Which of the following BEST describes the type of attack that is occurring?

Which of the following BEST describes the type of attack that is occurring?
Question 339
Ann, a customer, received a notification from her mortgage company stating her PII may be shared with partners, affiliates, and associates to maintain day-to-day business operations.
Which of the following documents did Ann receive?
Which of the following documents did Ann receive?
Question 340
A network engineer needs to create a plan for upgrading the wireless infrastructure in a large office Priority must be given to areas that are currently experiencing latency and connection issues. Which of the following would be the BEST resource for determining the order of priority?

