Question 46
Local guidelines require that all information systems meet a minimum-security baseline to be compliant. Which of the following can security administrators use to assess their system configurations against the baseline?
Question 47
A security manager runs Nessus scans of the network after every maintenance window. Which of the following is the security manger MOST likely trying to accomplish?
Question 48
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
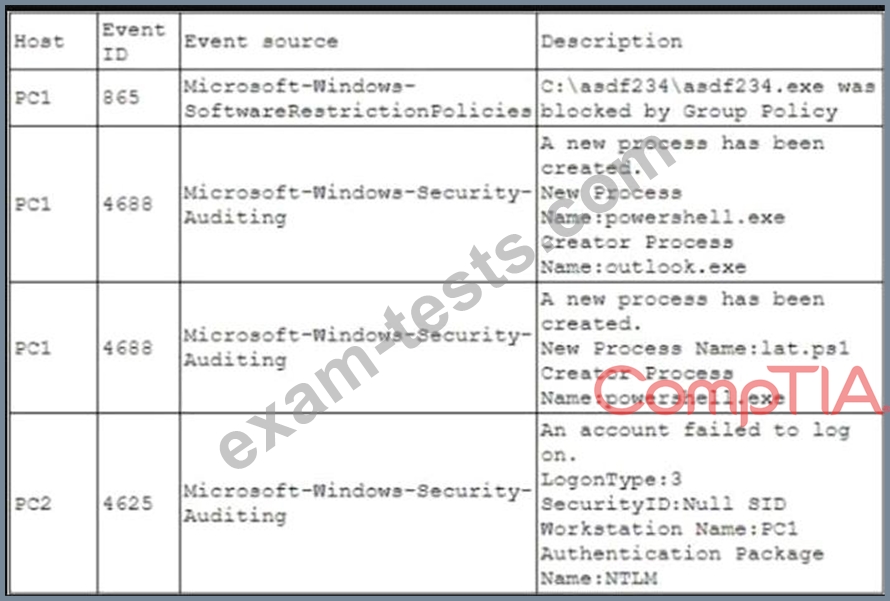
Which of the following describes the method that was used to compromise the laptop?

Which of the following describes the method that was used to compromise the laptop?
Question 49
An organization has implemented a two-step verification process to protect user access to data that 6 stored in the could Each employee now uses an email address of mobile number a code to access the dat a. Which of the following authentication methods did the organization implement?
Question 50
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to connect network traffic between workstation throughout the network. The analysts review the following logs:
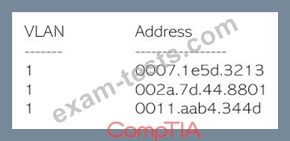
The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?

The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?

