Question 31
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following slops:
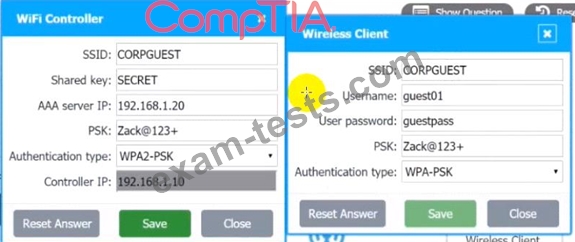
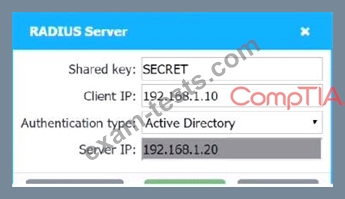
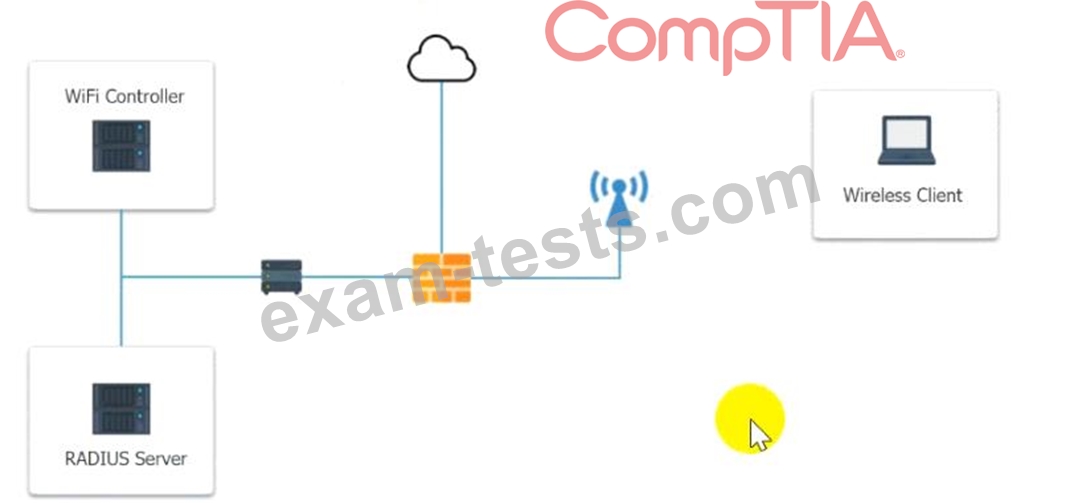
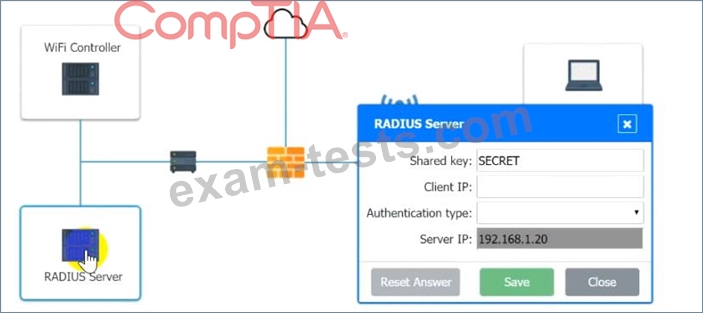
1. Configure the RADIUS server.
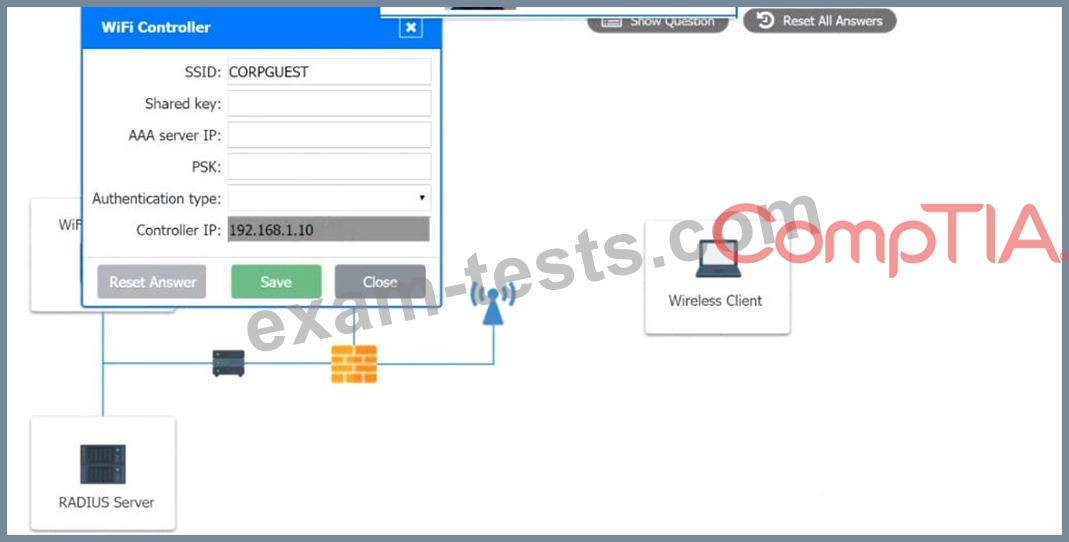
2. Configure the WiFi controller.
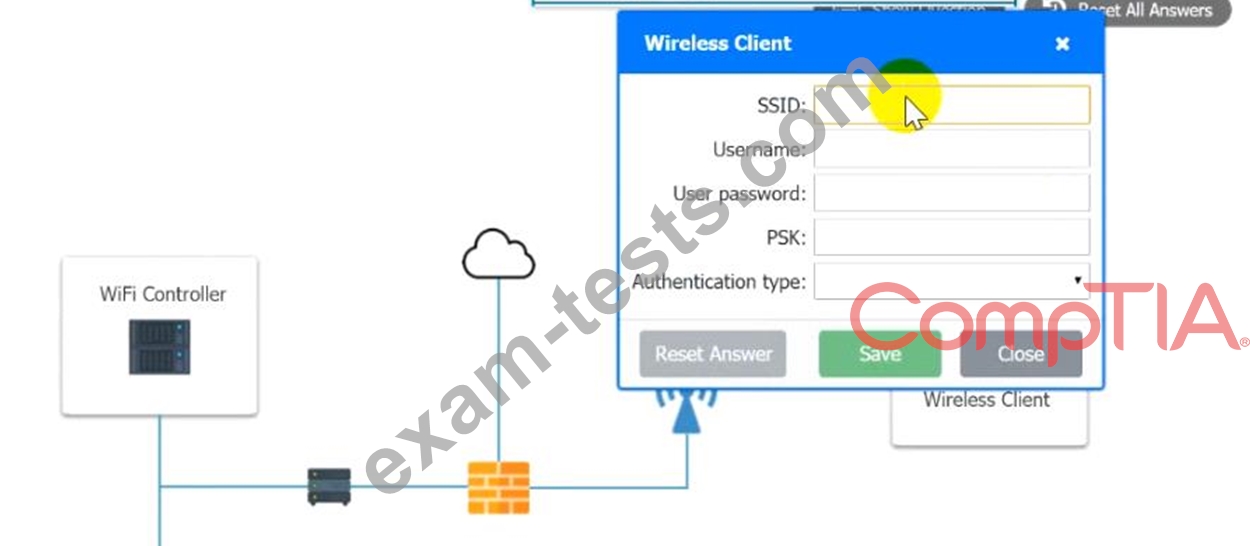
3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01
Password: guestpass
Perform the following slops:
1. Configure the RADIUS server.
2. Configure the WiFi controller.
3. Preconfigure the client for an incoming guest. The guest AD credentials are:
User: guest01
Password: guestpass




Question 32
A web server administrator has redundant servers and needs to ensure failover to the secondary server when the primary server goes down. Which of the following should the administrator implement to avoid disruption?
Question 33
During an incident response, an analyst applied rules to all inbound traffic on the border firewall and implemented ACLs on each critical server. Following an investigation, the company realizes it is still vulnerable because outbound traffic is not restricted, and the adversary is able to maintain a presence in the network. In which of the following stages of the Cyber Kill Chain is the adversary currently operating?
Question 34
Which of the following provides the BEST protection for sensitive information and data stored in cloud-based services but still allows for full functionality and searchability of data within the cloud-based services?
Question 35
Which of the following should a technician consider when selecting an encryption method for data that needs to remain confidential for a specific length of time?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: