Question 1
A cybersecurity manager has scheduled biannual meetings with the IT team and department leaders to discuss how they would respond to hypothetical cyberattacks. During these meetings, the manager presents a scenario and injects additional information throughout the session to replicate what might occur in a dynamic cybersecurity event involving the company, its facilities, its data, and its staff. Which of the following describes what the manager is doing?
Question 2
Joe. a security analyst, recently performed a network discovery to fully understand his organization's electronic footprint from a "public" perspective. Joe ran a set of commands and received the following output:
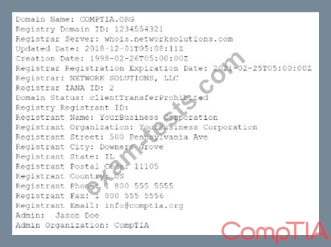
Which of the following can be determined about the organization's public presence and security posture? (Select TWO).

Which of the following can be determined about the organization's public presence and security posture? (Select TWO).
Question 3
Developers are writing code and merging it into shared repositories several times a day, where it is tested automatically. Which of the following concepts does this BEST represent?
Question 4
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing?
Question 5
A penetration tester successfully gained access to a company's network The investigating analyst determines malicious traffic connected through the WAP despite filtering rules being in place. Logging in to the connected switch, the analyst sees the following m the ARP table:
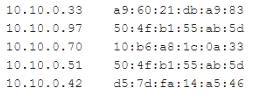
Which of the following did Ihe penetration tester MOST likely use?

Which of the following did Ihe penetration tester MOST likely use?

