Question 81
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
Question 82
An analyst is generating a security report for the management team. Security guidelines recommend disabling all listening unencrypted services. Given this output from Nmap.
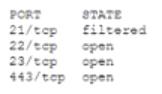
Which of the following should the analyst recommend to disable?

Which of the following should the analyst recommend to disable?
Question 83
Given the following logs:

Which of the following BEST describes the type of attack that is occurring?

Which of the following BEST describes the type of attack that is occurring?
Question 84
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery?
Question 85
Which of the following controls would BEST identify and report malicious insider activities?

