Question 96
An organization relies on third-party video conferencing to conduct daily business. Recent security changes now require all remote workers to utilize a VPN to corporate resources. Which of the following would BEST maintain high-quality video conferencing while minimizing latency when connected to the VPN?
Question 97
A security analyst discovers several .jpg photos from a cellular phone during a forensics investigation involving a compromised system. The analyst runs a forensics tool to gather file metadat a. Which of the following would be part of the images if all the metadata is still intact?
Question 98
A financial institution would like to stare is customer data a could but still allow the data ta he accessed and manipulated while encrypted. Doing se would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution is not concern about computational overheads and slow speeds, Which of the following cryptographic techniques would BEST meet the requirement?
Question 99
While investigating a data leakage incident, a security analyst reviews access control to cloud-hosted dat a. The following information was presented in a security posture report.
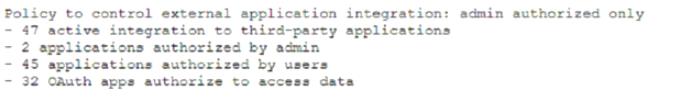
Based on the report, which of the following was the MOST likely attack vector used against the company?

Based on the report, which of the following was the MOST likely attack vector used against the company?
Question 100
A security analyst is investigation an incident that was first reported as an issue connecting to network shares and the internet, While reviewing logs and tool output, the analyst sees the following:

Which of the following attacks has occurred?

Which of the following attacks has occurred?

