Question 126
A startup company is using multiple SaaS and IaaS platforms to stand up a corporate infrastructure and build out a customer-facing web application. Which of the following solutions would be BEST to provide security, manageability, and visibility into the platforms?
Question 127
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host:

Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?

Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?
Question 128
A forensics investigator is examining a number of unauthorized payments that were reported on the 00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
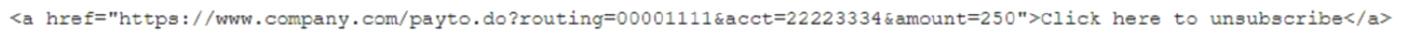
Which of the following will the forensics investigator MOST likely determine has occurred?
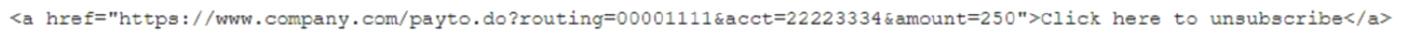
Which of the following will the forensics investigator MOST likely determine has occurred?
Question 129
Which of the following BEST explains the reason why a server administrator would place a document named password.txt on the desktop of an administrator account on a server?
Question 130
Company engineers regularly participate in a public Internet forum with other engineers throughout the industry. Which of the following tactics would an attacker MOST likely use in this scenario?

