Question 121
A security analyst receives the configuration of a current VPN profile and notices the authentication is only applied to the IP datagram portion of the packet. Which of the following should the analyst implement to authenticate the entire packet?
Question 122
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls? (Select TWO).
Question 123
A company just developed a new web application for a government agency. The application must be assessed and authorized prior to being deployed. Which of the following is required to assess the vulnerabilities resident in the application?
Question 124
Which of the following describes the BEST approach for deploying application patches?
Question 125
A security analyst is reviewing the following attack log output:
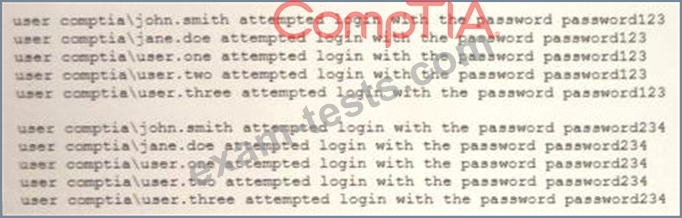
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?

