Question 51
An analyst visits an internet forum looking for information about a tool. The analyst finds a threat that appears to contain relevant information. One of the posts says the following:
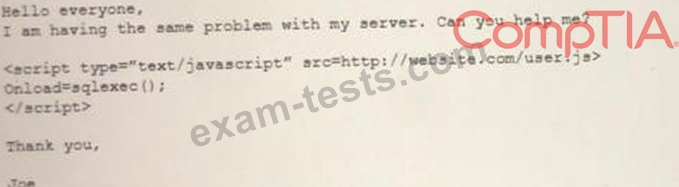
Which of the following BEST describes the attack that was attempted against the forum readers?

Which of the following BEST describes the attack that was attempted against the forum readers?
Question 52
A security analyst is logged into a Windows file server and needs to see who is accessing files and from which computers.
Which of the following tools should the analyst use?
Which of the following tools should the analyst use?
Question 53
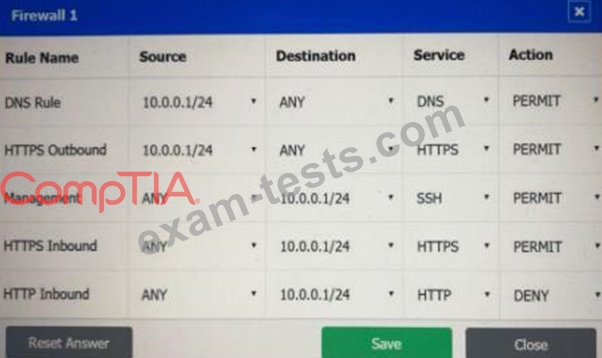
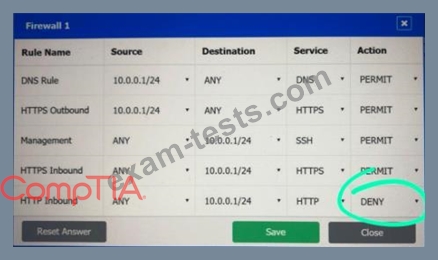
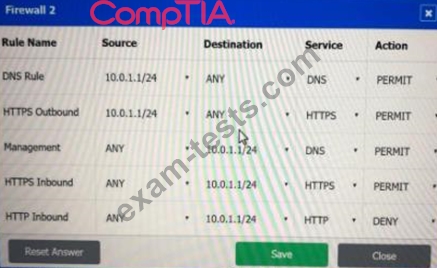
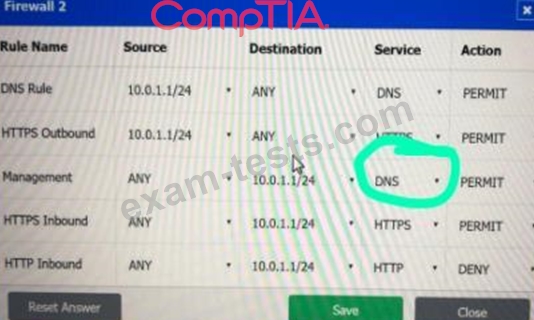
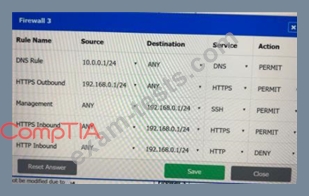
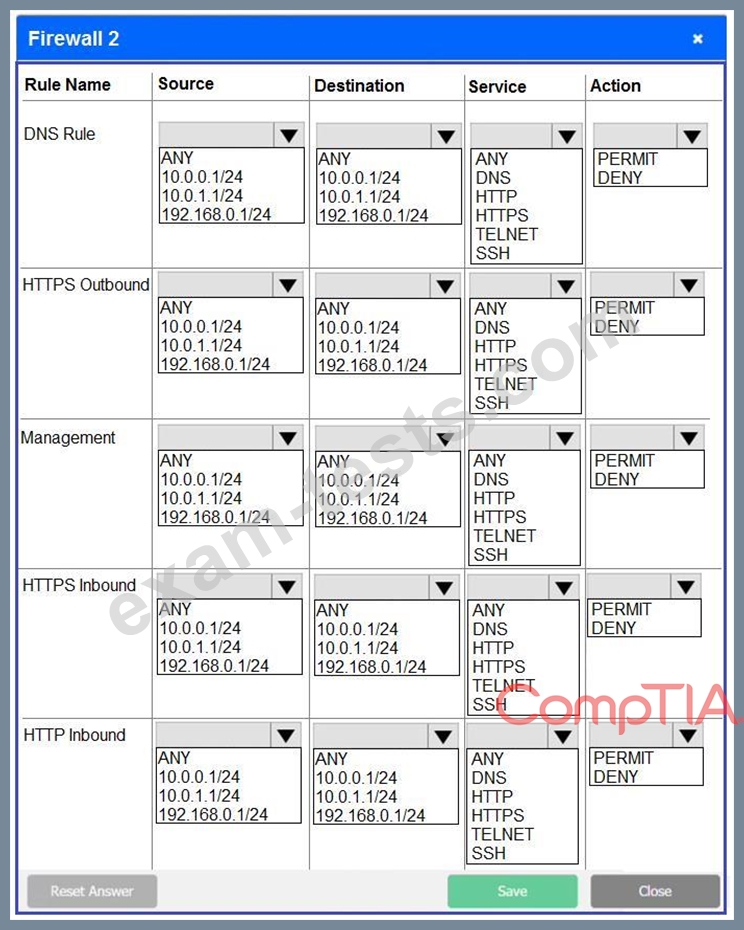
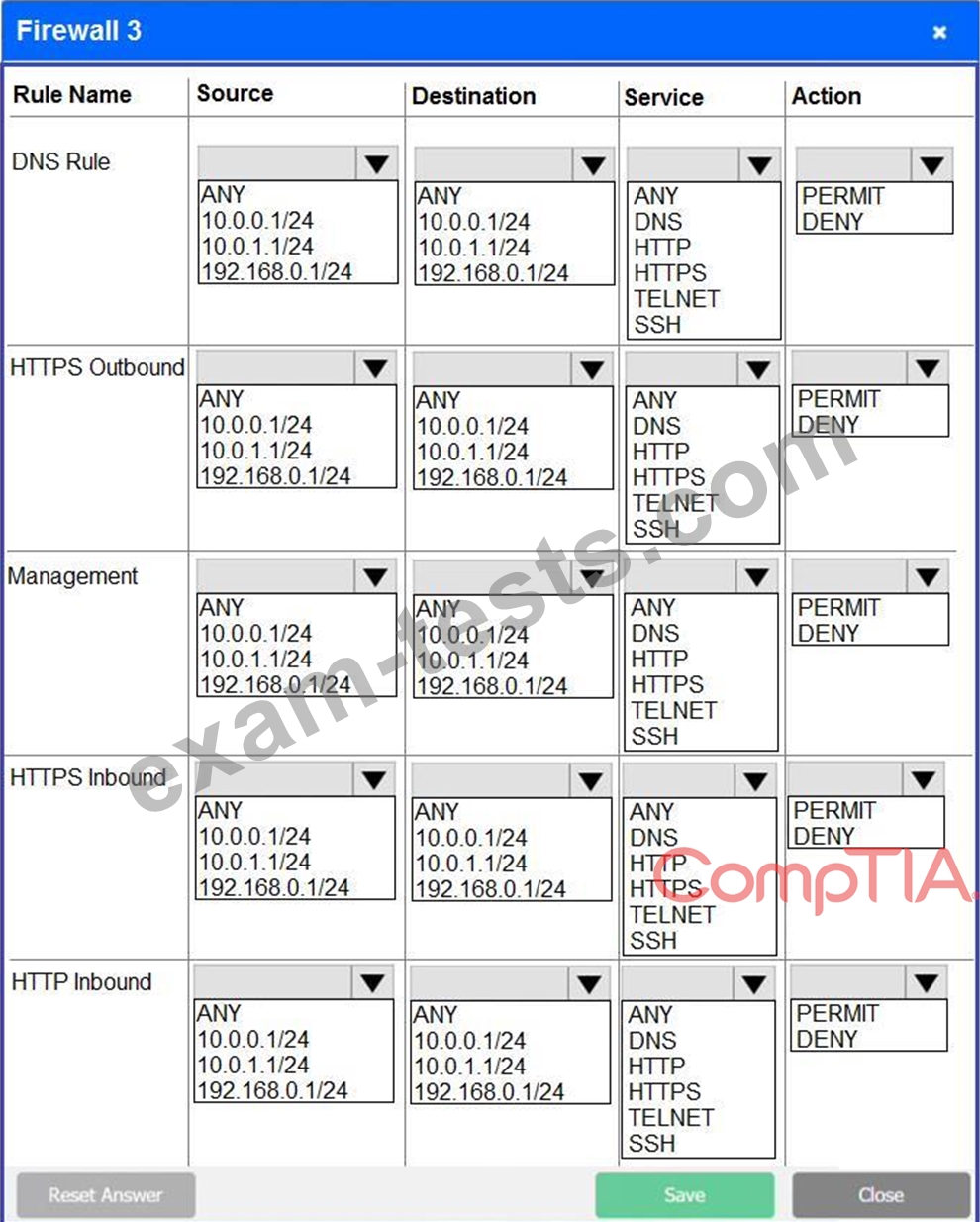
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
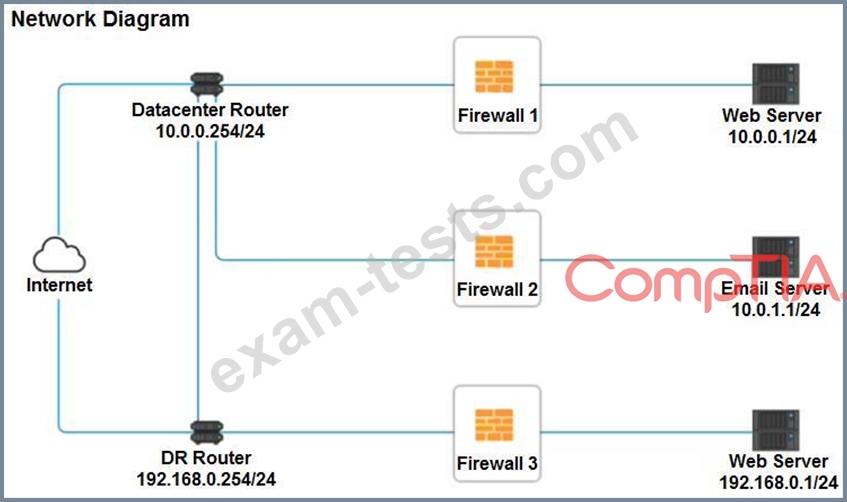
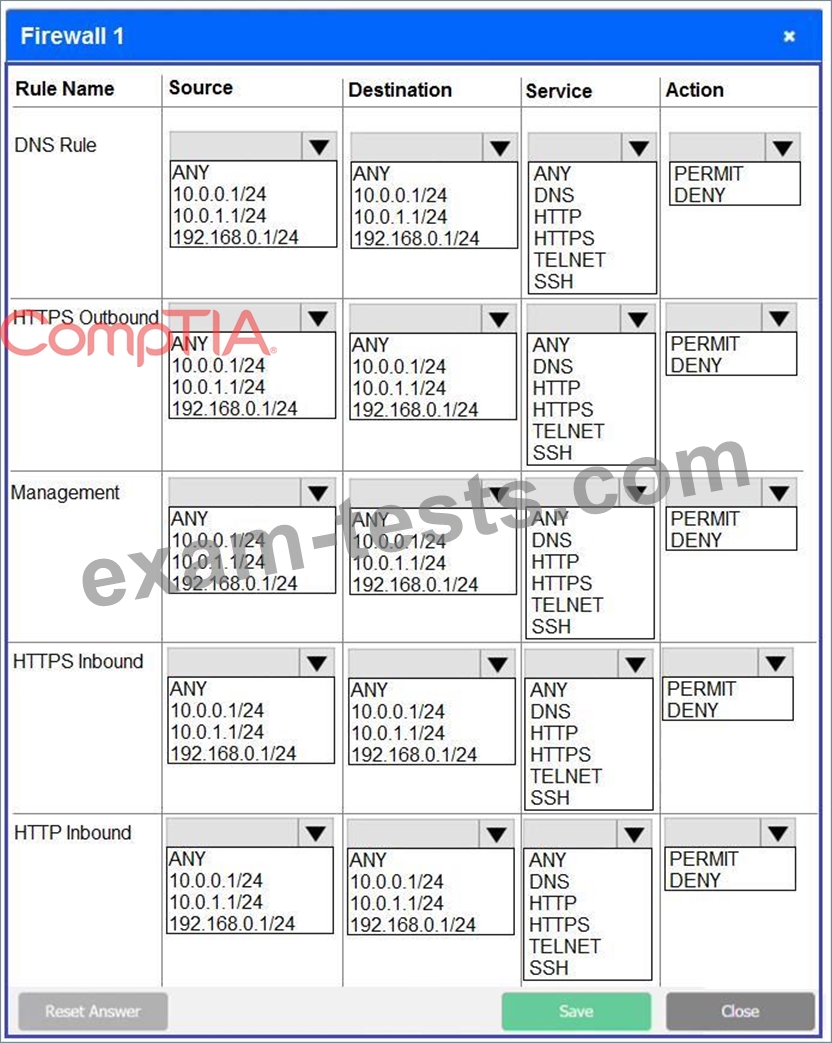
INSTRUCTIONS
Click on each firewall to do the following:
* Deny cleartext web traffic.
* Ensure secure management protocols are used.
* Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.




Question 54
When planning to build a virtual environment, an administrator need to achieve the following:
- Establish polices in Limit who can create new VMs
- Allocate resources according to actual utilization`
- Require justification for requests outside of the standard
requirements.
- Create standardized categories based on size and resource
requirements
Which of the following is the administrator MOST likely trying to do?
- Establish polices in Limit who can create new VMs
- Allocate resources according to actual utilization`
- Require justification for requests outside of the standard
requirements.
- Create standardized categories based on size and resource
requirements
Which of the following is the administrator MOST likely trying to do?
Question 55
A security engineer is installing a WAF to protect the company's website from malicious web requests over SSL. Which of the following is needed to meet the objective?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: